Chrome Extension Turns Malicious After Ownership Transfer, Enabling Code Injection and Data Theft
Two Google Chrome extensions have turned malicious after what appears to be a case of ownership transfer, offering…
March 9, 2026
Web Server Exploits and Mimikatz Used in Attacks Targeting Asian Critical Infrastructure
High-value organizations located in South, Southeast, and East Asia have been targeted by a Chinese threat actor as…
March 9, 2026
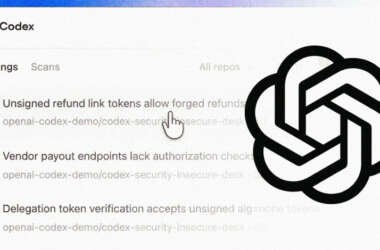
OpenAI Codex Security Scanned 1.2 Million Commits and Found 10,561 High-Severity Issues
OpenAI on Friday began rolling out Codex Security, an artificial intelligence (AI)-powered security agent that’s designed to find,…
March 7, 2026
Anthropic Finds 22 Firefox Vulnerabilities Using Claude Opus 4.6 AI Model
Anthropic on Friday said it discovered 22 new security vulnerabilities in the Firefox web browser as part of…
March 7, 2026
Transparent Tribe Uses AI to Mass-Produce Malware Implants in Campaign Targeting India
The Pakistan-aligned threat actor known as Transparent Tribe has become the latest hacking group to embrace artificial intelligence…
March 6, 2026
Multi-Stage VOID#GEIST Malware Delivering XWorm, AsyncRAT, and Xeno RAT
Cybersecurity researchers have disclosed details of a multi-stage malware campaign that uses batch scripts as a pathway to…
March 6, 2026
The MSP Guide to Using AI-Powered Risk Management to Scale Cybersecurity
Scaling cybersecurity services as an MSP or MSSP requires technical expertise and a business model that delivers measurable…
March 6, 2026
Iran-Linked MuddyWater Hackers Target U.S. Networks With New Dindoor Backdoor
New research from Broadcom’s Symantec and Carbon Black Threat Hunter Team has discovered evidence of an Iranian hacking…
March 6, 2026
China-Linked Hackers Use TernDoor, PeerTime, BruteEntry in South American Telecom Attacks
A China-linked advanced persistent threat (APT) actor has been targeting critical telecommunications infrastructure in South America since 2024,…
March 6, 2026
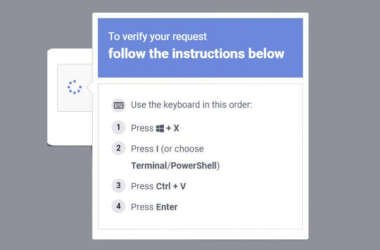
Microsoft Reveals ClickFix Campaign Using Windows Terminal to Deploy Lumma Stealer
Microsoft on Thursday disclosed details of a new widespread ClickFix social engineering campaign that has leveraged the Windows…
March 6, 2026