From Quantum Hacks to AI Defenses – Expert Guide to Building Unbreakable Cyber Resilience
Quantum computing and AI working together will bring incredible opportunities. Together, the technologies will help us extend innovation…
September 17, 2025
Rethinking AI Data Security: A Buyer’s Guide
Generative AI has gone from a curiosity to a cornerstone of enterprise productivity in just a few short…
September 17, 2025
Scattered Spider Resurfaces With Financial Sector Attacks Despite Retirement Claims
Cybersecurity researchers have tied a fresh round of cyber attacks targeting financial services to the notorious cybercrime group…
September 17, 2025
DOJ Resentences BreachForums Founder to 3 Years for Cybercrime and Possession of CSAM
The U.S. Department of Justice (DoJ) on Tuesday resentenced the former administrator of BreachForums to three years in…
September 17, 2025
SlopAds Fraud Ring Exploits 224 Android Apps to Drive 2.3 Billion Daily Ad Bids
A massive ad fraud and click fraud operation dubbed SlopAds ran a cluster of 224 apps, collectively attracting…
September 16, 2025
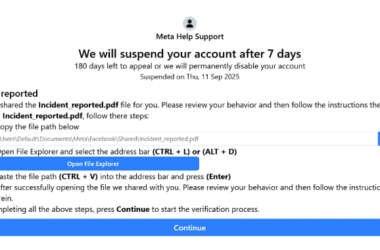
New FileFix Variant Delivers StealC Malware Through Multilingual Phishing Site
Cybersecurity researchers have warned of a new campaign that’s leveraging a variant of the FileFix social engineering tactic…
September 16, 2025
Apple Backports Fix for CVE-2025-43300 Exploited in Sophisticated Spyware Attack
Apple on Monday backported fixes for a recently patched security flaw that has been actively exploited in the…
September 16, 2025
Securing the Agentic Era: Introducing Astrix’s AI Agent Control Plane
AI agents are rapidly becoming a core part of the enterprise, being embedded across enterprise workflows, operating with…
September 16, 2025
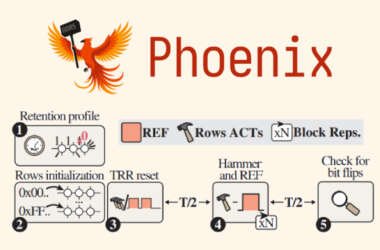
Phoenix RowHammer Attack Bypasses Advanced DDR5 Memory Protections in 109 Seconds
A team of academics from ETH Zürich and Google has discovered a new variant of a RowHammer attack…
September 16, 2025
6 Browser-Based Attacks Security Teams Need to Prepare For Right Now
Attacks that target users in their web browsers have seen an unprecedented rise in recent years. In this…
September 15, 2025