TAG-150 Develops CastleRAT in Python and C, Expanding CastleLoader Malware Operations
The threat actor behind the malware-as-a-service (MaaS) framework and loader called CastleLoader has also developed a remote access…
September 5, 2025
SAP S/4HANA Critical Vulnerability CVE-2025-42957 Exploited in the Wild
A critical security vulnerability impacting SAP S/4HANA, an Enterprise Resource Planning (ERP) software, has come under active exploitation…
September 5, 2025
Automation Is Redefining Pentest Delivery
Pentesting remains one of the most effective ways to identify real-world security weaknesses before adversaries do. But as…
September 5, 2025
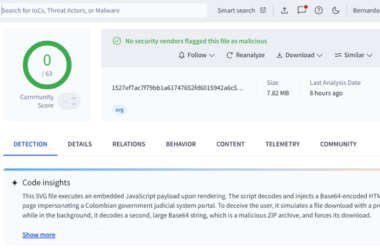
VirusTotal Finds 44 Undetected SVG Files Used to Deploy Base64-Encoded Phishing Pages
Cybersecurity researchers have flagged a new malware campaign that has leveraged Scalable Vector Graphics (SVG) files as part…
September 5, 2025
Russian APT28 Deploys “NotDoor” Outlook Backdoor Against Companies in NATO Countries
The Russian state-sponsored hacking group tracked as APT28 has been attributed to a new Microsoft Outlook backdoor called…
September 4, 2025
Cybercriminals Exploit X’s Grok AI to Bypass Ad Protections and Spread Malware to Millions
Cybersecurity researchers have flagged a new technique that cybercriminals have adopted to bypass social media platform X’s malvertising…
September 4, 2025
Google Fined $379 Million by French Regulator for Cookie Consent Violations
The French data protection authority has fined Google and Chinese e-commerce giant Shein $379 million (€325 million) and…
September 4, 2025
CISA Flags TP-Link Router Flaws CVE-2023-50224 and CVE-2025-9377 as Actively Exploited
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security flaws impacting TP-Link wireless routers…
September 4, 2025
Malicious npm Packages Exploit Ethereum Smart Contracts to Target Crypto Developers
Cybersecurity researchers have discovered two new malicious packages on the npm registry that make use of smart contracts…
September 3, 2025
Threat Actors Weaponize HexStrike AI to Exploit Citrix Flaws Within a Week of Disclosure
Threat actors are attempting to leverage a newly released artificial intelligence (AI) offensive security tool called HexStrike AI…
September 3, 2025