ShadowCaptcha Exploits WordPress Sites to Spread Ransomware, Info Stealers, and Crypto Miners
A new large-scale campaign has been observed exploiting over 100 compromised WordPress sites to direct site visitors to…
August 26, 2025
HOOK Android Trojan Adds Ransomware Overlays, Expands to 107 Remote Commands
Cybersecurity researchers have discovered a new variant of an Android banking trojan called HOOK that features ransomware-style overlay…
August 26, 2025
Google to Verify All Android Developers in 4 Countries to Block Malicious Apps
Google has announced plans to begin verifying the identity of all developers who distribute apps on Android, even…
August 26, 2025
⚡ Weekly Recap: Password Manager Flaws, Apple 0-Day, Hidden AI Prompts, In-the-Wild Exploits & More
Cybersecurity today moves at the pace of global politics. A single breach can ripple across supply chains, turn…
August 25, 2025
Why SIEM Rules Fail and How to Fix Them: Insights from 160 Million Attack Simulations
Security Information and Event Management (SIEM) systems act as the primary tools for detecting suspicious activity in enterprise…
August 25, 2025
Transparent Tribe Targets Indian Govt With Weaponized Desktop Shortcuts via Phishing
The advanced persistent threat (APT) actor known as Transparent Tribe has been observed targeting both Windows and BOSS…
August 25, 2025
Malicious Go Module Poses as SSH Brute-Force Tool, Steals Credentials via Telegram Bot
Cybersecurity researchers have discovered a malicious Go module that presents itself as a brute-force tool for SSH but…
August 24, 2025
GeoServer Exploits, PolarEdge, and Gayfemboy Push Cybercrime Beyond Traditional Botnets
Cybersecurity researchers are calling attention to multiple campaigns that leverage known security vulnerabilities and expose Redis servers to…
August 23, 2025
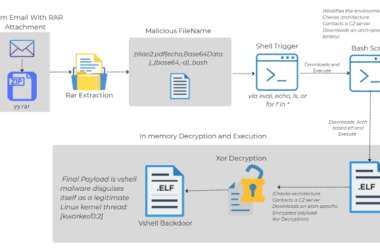
Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source…
August 22, 2025
Automation Is Redefining Pentest Delivery
Pentesting remains one of the most effective ways to identify real-world security weaknesses before adversaries do. But as…
August 22, 2025