AI SOC 101: Key Capabilities Security Leaders Need to Know
Security operations have never been a 9-to-5 job. For SOC analysts, the day often starts and ends deep…
August 13, 2025
Webinar: What the Next Wave of AI Cyberattacks Will Look Like — And How to Survive
The AI revolution isn’t coming. It’s already here. From copilots that write our emails to autonomous agents that…
August 13, 2025
Microsoft August 2025 Patch Tuesday Fixes Kerberos Zero-Day Among 111 Total New Flaws
Microsoft on Tuesday rolled out fixes for a massive set of 111 security flaws across its software portfolio,…
August 13, 2025
New ‘Curly COMrades’ APT Using NGEN COM Hijacking in Georgia, Moldova Attacks
A previously undocumented threat actor dubbed Curly COMrades has been observed targeting entities in Georgia and Moldova as…
August 12, 2025
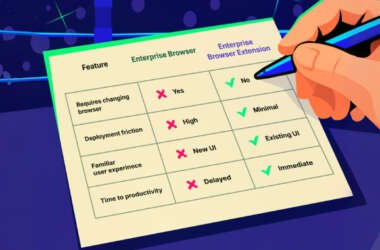
The Ultimate Battle: Enterprise Browsers vs. Secure Browser Extensions
Most security tools can’t see what happens inside the browser, but that’s where the majority of work, and…
August 12, 2025
Dutch NCSC Confirms Active Exploitation of Citrix NetScaler CVE-2025-6543 in Critical Sectors
The Dutch National Cyber Security Centre (NCSC-NL) has warned of cyber attacks exploiting a recently disclosed critical security…
August 12, 2025
New TETRA Radio Encryption Flaws Expose Law Enforcement Communications
Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial Trunked Radio (TETRA) communications protocol,…
August 11, 2025
Researchers Spot Surge in Erlang/OTP SSH RCE Exploits, 70% Target OT Firewalls
Malicious actors have been observed exploiting a now-patched critical security flaw impacting Erlang/Open Telecom Platform (OTP) SSH as…
August 11, 2025
⚡ Weekly Recap: BadCam Attack, WinRAR 0-Day, EDR Killer, NVIDIA Flaws, Ransomware Attacks & More
This week, cyber attackers are moving quickly, and businesses need to stay alert. They’re finding new weaknesses in…
August 11, 2025
6 Lessons Learned: Focusing Security Where Business Value Lives
The Evolution of Exposure Management Most security teams have a good sense of what’s critical in their environment.…
August 11, 2025