WinRAR Zero-Day Under Active Exploitation – Update to Latest Version Immediately
The maintainers of the WinRAR file archiving utility have released an update to address an actively exploited zero-day…
August 11, 2025
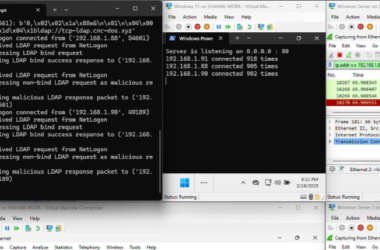
New Win-DDoS Flaws Let Attackers Turn Public Domain Controllers into DDoS Botnet via RPC, LDAP
A novel attack technique could be weaponized to rope thousands of public domain controllers (DCs) around the world…
August 10, 2025
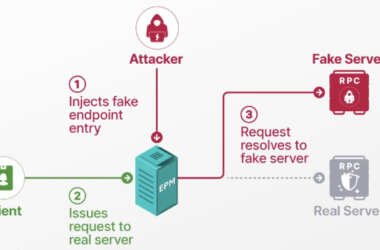
Researchers Detail Windows EPM Poisoning Exploit Chain Leading to Domain Privilege Escalation
Cybersecurity researchers have presented new findings related to a now-patched security issue in Microsoft’s Windows Remote Procedure Call…
August 10, 2025
Linux-Based Lenovo Webcams’ Flaw Can Be Remotely Exploited for BadUSB Attacks
Cybersecurity researchers have disclosed vulnerabilities in select model webcams from Lenovo that could turn them into BadUSB attack…
August 9, 2025
Researchers Reveal ReVault Attack Targeting Dell ControlVault3 Firmware in 100+ Laptop Models
Cybersecurity researchers have uncovered multiple security flaws in Dell’s ControlVault3 firmware and its associated Windows APIs that could…
August 9, 2025
Researchers Uncover GPT-5 Jailbreak and Zero-Click AI Agent Attacks Exposing Cloud and IoT Systems
Cybersecurity researchers have uncovered a jailbreak technique to bypass ethical guardrails erected by OpenAI in its latest large…
August 9, 2025
CyberArk and HashiCorp Flaws Enable Remote Vault Takeover Without Credentials
Cybersecurity researchers have discovered over a dozen vulnerabilities in enterprise secure vaults from CyberArk and HashiCorp that, if…
August 9, 2025
AI Tools Fuel Brazilian Phishing Scam While Efimer Trojan Steals Crypto from 5,000 Victims
Cybersecurity researchers are drawing attention to a new campaign that’s using legitimate generative artificial intelligence (AI)-powered website building…
August 8, 2025
Leaked Credentials Up 160%: What Attackers Are Doing With Them
When an organization’s credentials are leaked, the immediate consequences are rarely visible—but the long-term impact is far-reaching. Far…
August 8, 2025
RubyGems, PyPI Hit by Malicious Packages Stealing Credentials, Crypto, Forcing Security Changes
A fresh set of 60 malicious packages has been uncovered targeting the RubyGems ecosystem by posing as seemingly…
August 8, 2025