GreedyBear Steals $1M in Crypto Using 150+ Malicious Firefox Wallet Extensions
A newly discovered campaign dubbed GreedyBear has leveraged over 150 malicious extensions to the Firefox marketplace that are…
August 8, 2025
SocGholish Malware Spread via Ad Tools; Delivers Access to LockBit, Evil Corp, and Others
The threat actors behind the SocGholish malware have been observed leveraging Traffic Distribution Systems (TDSs) like Parrot TDS…
August 7, 2025
Webinar: How to Stop Python Supply Chain Attacks—and the Expert Tools You Need
Python is everywhere in modern software. From machine learning models to production microservices, chances are your code—and your…
August 7, 2025
Malicious Go, npm Packages Deliver Cross-Platform Malware, Trigger Remote Data Wipes
Cybersecurity researchers have discovered a set of 11 malicious Go packages that are designed to download additional payloads…
August 7, 2025
The AI-Powered Security Shift: What 2025 Is Teaching Us About Cloud Defense
Now that we are well into 2025, cloud attacks are evolving faster than ever and artificial intelligence (AI)…
August 7, 2025
Microsoft Discloses Exchange Server Flaw Enabling Silent Cloud Access in Hybrid Setups
Microsoft has released an advisory for a high-severity security flaw affecting on-premise versions of Exchange Server that could…
August 7, 2025
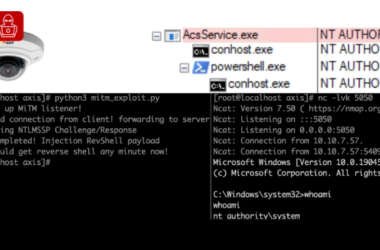
6,500 Axis Servers Expose Remoting Protocol, 4,000 in U.S. Vulnerable to Exploits
Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis Communications that, if successfully exploited,…
August 7, 2025
SonicWall Confirms Patched Vulnerability Behind Recent VPN Attacks, Not a Zero-Day
SonicWall has revealed that the recent spike in activity targeting its Gen 7 and newer firewalls with SSL…
August 7, 2025
AI Slashes Workloads for vCISOs by 68% as SMBs Demand More – New Report Reveals
As the volume and sophistication of cyber threats and risks grow, cybersecurity has become mission-critical for businesses of…
August 6, 2025
Microsoft Launches Project Ire to Autonomously Classify Malware Using AI Tools
Microsoft on Tuesday announced an autonomous artificial intelligence (AI) agent that can analyze and classify software without assistance…
August 6, 2025