U.S. Sanctions Firm Behind N. Korean IT Scheme; Arizona Woman Jailed for Running Laptop Farm
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned a North Korean front company…
July 25, 2025
Patchwork Targets Turkish Defense Firms with Spear-Phishing Using Malicious LNK Files
The threat actor known as Patchwork has been attributed to a new spear-phishing campaign targeting Turkish defense contractors…
July 25, 2025
Cyber Espionage Campaign Hits Russian Aerospace Sector Using EAGLET Backdoor
Russian aerospace and defense industries have become the target of a cyber espionage campaign that delivers a backdoor…
July 25, 2025
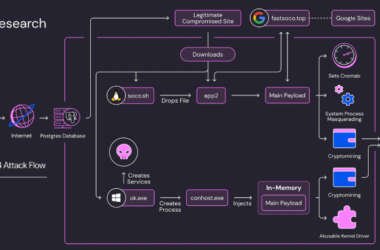
Soco404 and Koske Malware Target Cloud Services with Cross-Platform Cryptomining Attacks
Threat hunters have disclosed two different malware campaigns that have targeted vulnerabilities and misconfigurations across cloud environments to…
July 25, 2025
Overcoming Risks from Chinese GenAI Tool Usage
A recent analysis of enterprise data suggests that generative AI tools developed in China are being used extensively…
July 25, 2025
Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices
Sophos and SonicWall have alerted users of critical security flaws in Sophos Firewall and Secure Mobile Access (SMA)…
July 24, 2025
Watch This Webinar to Uncover Hidden Flaws in Login, AI, and Digital Trust — and Fix Them
Is Managing Customer Logins and Data Giving You Headaches? You’re Not Alone! Today, we all expect super-fast, secure,…
July 24, 2025
Pentests once a year? Nope. It’s time to build an offensive SOC
You wouldn’t run your blue team once a year, so why accept this substandard schedule for your offensive…
July 24, 2025
China-Based APTs Deploy Fake Dalai Lama Apps to Spy on Tibetan Community
The Tibetan community has been targeted by a China-nexus cyber espionage group as part of two campaigns conducted…
July 24, 2025
Storm-2603 Exploits SharePoint Flaws to Deploy Warlock Ransomware on Unpatched Systems
Microsoft has revealed that one of the threat actors behind the active exploitation of SharePoint flaws is deploying…
July 24, 2025