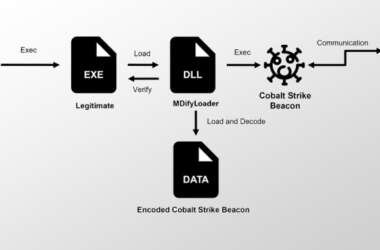
Ivanti Zero-Days Exploited to Drop MDifyLoader and Launch In-Memory Cobalt Strike Attacks
Cybersecurity researchers have disclosed details of a new malware called MDifyLoader that has been observed in conjunction with…
July 18, 2025
CERT-UA Discovers LAMEHUG Malware Linked to APT28, Using LLM for Phishing Campaign
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of a phishing campaign that’s designed to…
July 18, 2025
Critical NVIDIA Container Toolkit Flaw Allows Privilege Escalation on AI Cloud Services
Cybersecurity researchers have disclosed a critical container escape vulnerability in the NVIDIA Container Toolkit that could pose a…
July 18, 2025
Google Sues 25 Chinese Entities Over BADBOX 2.0 Botnet Affecting 10M Android Devices
Google on Thursday revealed it’s pursuing legal action in New York federal court against 25 unnamed individuals or…
July 18, 2025
From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware
With IT outages and disruptions escalating, IT teams are shifting their focus beyond simply backing up data to…
July 18, 2025
Hackers Use GitHub Repositories to Host Amadey Malware and Data Stealers, Bypassing Filters
Threat actors are leveraging public GitHub repositories to host malicious payloads and distribute them via Amadey as part…
July 17, 2025
Hackers Exploit Apache HTTP Server Flaw to Deploy Linuxsys Cryptocurrency Miner
Cybersecurity researchers have discovered a new campaign that exploits a known security flaw impacting Apache HTTP Server to…
July 17, 2025
Europol Disrupts NoName057(16) Hacktivist Group Linked to DDoS Attacks Against Ukraine
An international operation coordinated by Europol has disrupted the infrastructure of a pro-Russian hacktivist group known as NoName057(16)…
July 17, 2025
CTEM vs ASM vs Vulnerability Management: What Security Leaders Need to Know in 2025
The modern-day threat landscape requires enterprise security teams to think and act beyond traditional cybersecurity measures that are…
July 17, 2025
Chinese Hackers Target Taiwan’s Semiconductor Sector with Cobalt Strike, Custom Backdoors
The Taiwanese semiconductor industry has become the target of spear-phishing campaigns undertaken by three Chinese state-sponsored threat actors.…
July 17, 2025