6 Steps to 24/7 In-House SOC Success
Hackers never sleep, so why should enterprise defenses? Threat actors prefer to target businesses during off-hours. That’s when…
June 20, 2025
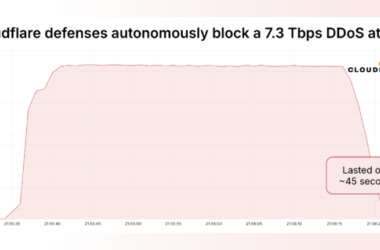
Massive 7.3 Tbps DDoS Attack Delivers 37.4 TB in 45 Seconds, Targeting Hosting Provider
Cloudflare on Thursday said it autonomously blocked the largest ever distributed denial-of-service (DDoS) attack ever recorded, which hit…
June 20, 2025
200+ Trojanized GitHub Repositories Found in Campaign Targeting Gamers and Developers
Cybersecurity researchers have uncovered a new campaign in which the threat actors have published more than 67 GitHub…
June 20, 2025
New Android Malware Surge Hits Devices via Overlays, Virtualization Fraud and NFC Theft
Cybersecurity researchers have exposed the inner workings of an Android malware called AntiDot that has compromised over 3,775…
June 19, 2025
BlueNoroff Deepfake Zoom Scam Hits Crypto Employee with MacOS Backdoor Malware
The North Korea-aligned threat actor known as BlueNoroff has been observed targeting an employee in the Web3 sector…
June 19, 2025
Secure Vibe Coding: The Complete New Guide
DALL-E for coders? That’s the promise behind vibe coding, a term describing the use of natural language to…
June 19, 2025
Uncover LOTS Attacks Hiding in Trusted Tools — Learn How in This Free Expert Session
Most cyberattacks today don’t start with loud alarms or broken firewalls. They start quietly—inside tools and websites your…
June 19, 2025
Russian APT29 Exploits Gmail App Passwords to Bypass 2FA in Targeted Phishing Campaign
Threat actors with suspected ties to Russia have been observed taking advantage of a Google account feature called…
June 19, 2025
Meta Adds Passkey Login Support to Facebook for Android and iOS Users
Meta Platforms on Wednesday announced that it’s adding support for passkeys, the next-generation password standard, on Facebook. “Passkeys…
June 19, 2025
FedRAMP at Startup Speed: Lessons Learned
For organizations eyeing the federal market, FedRAMP can feel like a gated fortress. With strict compliance requirements and…
June 18, 2025