Playbook: Transforming Your Cybersecurity Practice Into An MRR Machine
Introduction The cybersecurity landscape is evolving rapidly, and so are the cyber needs of organizations worldwide. While businesses…
June 16, 2025
Malicious PyPI Package Masquerades as Chimera Module to Steal AWS, CI/CD, and macOS Data
Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that’s capable of harvesting…
June 16, 2025
Discord Invite Link Hijacking Delivers AsyncRAT and Skuld Stealer Targeting Crypto Wallets
A new malware campaign is exploiting a weakness in Discord’s invitation system to deliver an information stealer called…
June 14, 2025
Over 269,000 Websites Infected with JSFireTruck JavaScript Malware in One Month
Cybersecurity researchers are calling attention to a “large-scale campaign” that has been observed compromising legitimate websites with malicious…
June 13, 2025
Ransomware Gangs Exploit Unpatched SimpleHelp Flaws to Target Victims with Double Extortion
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday disclosed that ransomware actors are targeting unpatched SimpleHelp…
June 13, 2025
CTEM is the New SOC: Shifting from Monitoring Alerts to Measuring Risk
Introduction: Security at a Tipping Point Security Operations Centers (SOCs) were built for a different era, one defined…
June 13, 2025
Apple Zero-Click Flaw in Messages Exploited to Spy on Journalists Using Paragon Spyware
Apple has disclosed that a now-patched security flaw present in its Messages app was actively exploited in the…
June 13, 2025
WordPress Sites Turned Weapon: How VexTrio and Affiliates Run a Global Scam Network
The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been linked to other TDS services…
June 12, 2025
New TokenBreak Attack Bypasses AI Moderation with Single-Character Text Changes
Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large…
June 12, 2025
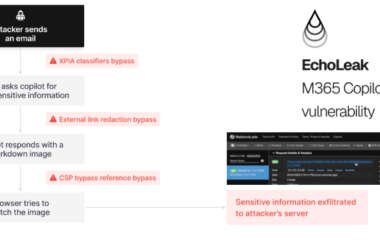
Zero-Click AI Vulnerability Exposes Microsoft 365 Copilot Data Without User Interaction
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows…
June 12, 2025