Preinstalled Apps on Ulefone, Krüger&Matz Phones Let Any App Reset Device, Steal PIN
Three security vulnerabilities have been disclosed in preloaded Android applications on smartphones from Ulefone and Krüger&Matz that could…
June 2, 2025
Qualcomm Fixes 3 Zero-Days Used in Targeted Android Attacks via Adreno GPU
Qualcomm has shipped security updates to address three zero-day vulnerabilities that it said have been exploited in limited,…
June 2, 2025
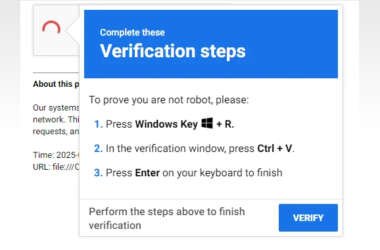
⚡ Weekly Recap: APT Intrusions, AI Malware, Zero-Click Exploits, Browser Hijacks and More
If this had been a security drill, someone would’ve said it went too far. But it wasn’t a…
June 2, 2025
The Secret Defense Strategy of Four Critical Industries Combating Advanced Cyber Threats
The evolution of cyber threats has forced organizations across all industries to rethink their security strategies. As attackers…
June 2, 2025
New Linux Flaws Allow Password Hash Theft via Core Dumps in Ubuntu, RHEL, Fedora
Two information disclosure flaws have been identified in apport and systemd-coredump, the core dump handlers in Ubuntu, Red…
May 31, 2025
U.S. DoJ Seizes 4 Domains Supporting Cybercrime Crypting Services in Global Operation
A multinational law enforcement operation has resulted in the takedown of an online cybercrime syndicate that offered services…
May 31, 2025
New EDDIESTEALER Malware Bypasses Chrome’s App-Bound Encryption to Steal Browser Data
A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social…
May 30, 2025
China-Linked Hackers Exploit SAP and SQL Server Flaws in Attacks Across Asia and Brazil
The China-linked threat actor behind the recent in-the-wild exploitation of a critical security flaw in SAP NetWeaver has…
May 30, 2025
From the “Department of No” to a “Culture of Yes”: A Healthcare CISO’s Journey to Enabling Modern Care
Breaking Out of the Security Mosh Pit When Jason Elrod, CISO of MultiCare Health System, describes legacy healthcare…
May 30, 2025
U.S. Sanctions Funnull for $200M Romance Baiting Scams Tied to Crypto Fraud
The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) has levied sanctions against a Philippines-based company…
May 30, 2025