From Infection to Access: A 24-Hour Timeline of a Modern Stealer Campaign
Stealer malware no longer just steals passwords. In 2025, it steals live sessions—and attackers are moving faster and…
May 28, 2025
New Self-Spreading Malware Infects Docker Containers to Mine Dero Cryptocurrency
Misconfigured Docker API instances have become the target of a new malware campaign that transforms them into a…
May 27, 2025
Cybercriminals Clone Antivirus Site to Spread Venom RAT and Steal Crypto Wallets
Cybersecurity researchers have disclosed a new malicious campaign that uses a fake website advertising antivirus software from Bitdefender…
May 27, 2025
Russian Hackers Breach 20+ NGOs Using Evilginx Phishing via Fake Microsoft Entra Pages
Microsoft has shed light on a previously undocumented cluster of malicious activity originating from a Russia-affiliated threat actor…
May 27, 2025
AI Agents and the Non‑Human Identity Crisis: How to Deploy AI More Securely at Scale
Artificial intelligence is driving a massive shift in enterprise productivity, from GitHub Copilot’s code completions to chatbots that mine…
May 27, 2025
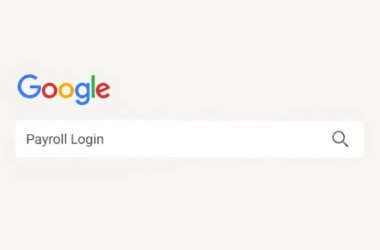
Employees Searching Payroll Portals on Google Tricked Into Sending Paychecks to Hackers
Threat hunters have exposed a novel campaign that makes use of search engine optimization (SEO) poisoning techniques to…
May 27, 2025
Over 70 Malicious npm and VS Code Packages Found Stealing Data and Crypto
As many as 60 malicious npm packages have been discovered in the package registry with malicious functionality to…
May 26, 2025
CISO’s Guide To Web Privacy Validation And Why It’s Important
Are your web privacy controls protecting your users, or just a box-ticking exercise? This CISO’s guide provides a…
May 26, 2025
⚡ Weekly Recap: APT Campaigns, Browser Hijacks, AI Malware, Cloud Breaches and Critical CVEs
Cyber threats don’t show up one at a time anymore. They’re layered, planned, and often stay hidden until…
May 26, 2025
Hackers Use Fake VPN and Browser NSIS Installers to Deliver Winos 4.0 Malware
Cybersecurity researchers have disclosed a malware campaign that uses fake software installers masquerading as popular tools like LetsVPN…
May 25, 2025