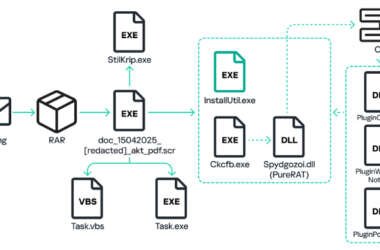
Russian Hackers Exploit Email and VPN Vulnerabilities to Spy on Ukraine Aid Logistics
Russian cyber threat actors have been attributed to a state-sponsored campaign targeting Western logistics entities and technology companies…
May 21, 2025
PureRAT Malware Spikes 4x in 2025, Deploying PureLogs to Target Russian Firms
Russian organizations have become the target of a phishing campaign that distributes malware called PureRAT, according to new…
May 21, 2025
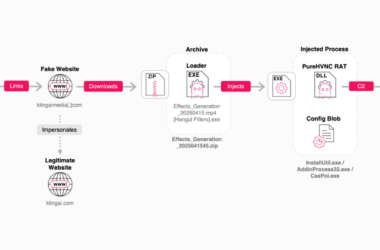
Fake Kling AI Facebook Ads Deliver RAT Malware to Over 22 Million Potential Victims
Counterfeit Facebook pages and sponsored ads on the social media platform are being employed to direct users to…
May 21, 2025
Securing CI/CD workflows with Wazuh
Continuous Integration and Continuous Delivery/Deployment (CI/CD) refers to practices that automate how code is developed and released to…
May 21, 2025
How to Detect Phishing Attacks Faster: Tycoon2FA Example
It takes just one email to compromise an entire system. A single well-crafted message can bypass filters, trick…
May 21, 2025
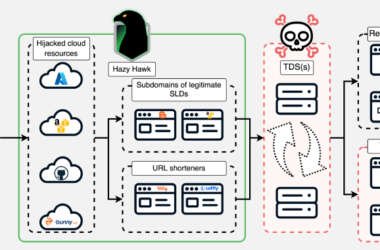
Hazy Hawk Exploits DNS Records to Hijack CDC, Corporate Domains for Malware Delivery
A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including…
May 20, 2025
100+ Fake Chrome Extensions Found Hijacking Sessions, Stealing Credentials, Injecting Ads
An unknown threat actor has been attributed to creating several malicious Chrome Browser extensions since February 2024 that…
May 20, 2025
AWS Default IAM Roles Found to Enable Lateral Movement and Cross-Service Exploitation
Cybersecurity researchers have discovered risky default identity and access management (IAM) roles impacting Amazon Web Services that could…
May 20, 2025
The Crowded Battle: Key Insights from the 2025 State of Pentesting Report
In the newly released 2025 State of Pentesting Report, Pentera surveyed 500 CISOs from global enterprises (200 from…
May 20, 2025
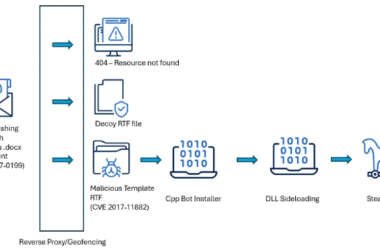
South Asian Ministries Hit by SideWinder APT Using Old Office Flaws and Custom Malware
High-level government institutions in Sri Lanka, Bangladesh, and Pakistan have emerged as the target of a new campaign…
May 20, 2025