China-Linked APTs Exploit SAP CVE-2025-31324 to Breach 581 Critical Systems Worldwide
A recently disclosed critical security flaw impacting SAP NetWeaver is being exploited by multiple China-nexus nation-state actors to…
May 13, 2025
Malicious PyPI Package Posing as Solana Tool Stole Source Code in 761 Downloads
Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that purports to be…
May 13, 2025
Deepfake Defense in the Age of AI
The cybersecurity landscape has been dramatically reshaped by the advent of generative AI. Attackers now leverage large language…
May 13, 2025
North Korean Konni APT Targets Ukraine with Malware to track Russian Invasion Progress
The North Korea-linked threat actor known as Konni APT has been attributed to a phishing campaign targeting government…
May 13, 2025
Moldovan Police Arrest Suspect in €4.5M Ransomware Attack on Dutch Research Agency
Moldovan law enforcement authorities have arrested a 45-year-old foreign man suspected of involvement in a series of ransomware…
May 13, 2025
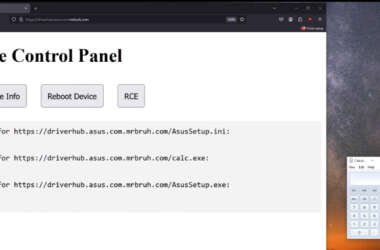
ASUS Patches DriverHub RCE Flaws Exploitable via HTTP and Crafted .ini Files
ASUS has released updates to address two security flaws impacting ASUS DriverHub that, if successfully exploited, could enable…
May 12, 2025
⚡ Weekly Recap: Zero-Day Exploits, Developer Malware, IoT Botnets, and AI-Powered Scams
What do a source code editor, a smart billboard, and a web server have in common? They’ve all…
May 12, 2025
The Persistence Problem: Why Exposed Credentials Remain Unfixed—and How to Change That
Detecting leaked credentials is only half the battle. The real challenge—and often the neglected half of the equation—is…
May 12, 2025
Fake AI Tools Used to Spread Noodlophile Malware, Targeting 62,000+ via Facebook Lures
Threat actors have been observed leveraging fake artificial intelligence (AI)-powered tools as a lure to entice users into…
May 12, 2025
Google Pays $1.375 Billion to Texas Over Unauthorized Tracking and Biometric Data Collection
Google has agreed to pay the U.S. state of Texas nearly $1.4 billion to settle two lawsuits that…
May 10, 2025