Claude AI Exploited to Operate 100+ Fake Political Personas in Global Influence Campaign
Artificial intelligence (AI) company Anthropic has revealed that unknown threat actors leveraged its Claude chatbot for an “influence-as-a-service”…
May 1, 2025
New Research Reveals: 95% of AppSec Fixes Don’t Reduce Risk
For over a decade, application security teams have faced a brutal irony: the more advanced the detection tools…
May 1, 2025
DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics
Russian companies have been targeted as part of a large-scale phishing campaign that’s designed to deliver a known…
May 1, 2025
Researchers Demonstrate How MCP Prompt Injection Can Be Used for Both Attack and Defense
As the field of artificial intelligence (AI) continues to evolve at a rapid pace, new research has found…
April 30, 2025
[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats
How Many Gaps Are Hiding in Your Identity System? It’s not just about logins anymore. Today’s attackers don’t…
April 30, 2025
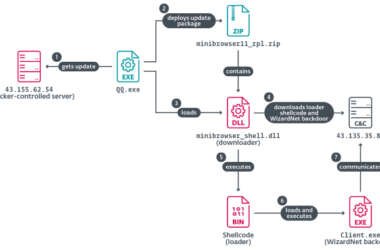
Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool
A China-aligned advanced persistent threat (APT) group called TheWizards has been linked to a lateral movement tool called…
April 30, 2025
Customer Account Takeovers: The Multi-Billion Dollar Problem You Don’t Know About
Everyone has cybersecurity stories involving family members. Here’s a relatively common one. The conversation usually goes something like…
April 30, 2025
Nebulous Mantis Targets NATO-Linked Entities with Multi-Stage Malware Attacks
Cybersecurity researchers have shed light on a Russian-speaking cyber espionage group called Nebulous Mantis that has deployed a…
April 30, 2025
WhatsApp Launches Private Processing to Enable AI Features While Protecting Message Privacy
Popular messaging app WhatsApp on Tuesday unveiled a new technology called Private Processing to enable artificial intelligence (AI)…
April 29, 2025
New Reports Uncover Jailbreaks, Unsafe Code, and Data Theft Risks in Leading AI Systems
Various generative artificial intelligence (GenAI) services have been found vulnerable to two types of jailbreak attacks that make…
April 29, 2025