North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures
North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute…
April 25, 2025
New Critical SAP NetWeaver Flaw Exploited to Drop Web Shell, Brute Ratel Framework
Threat actors are likely exploiting a new vulnerability in SAP NetWeaver to upload JSP web shells with the…
April 25, 2025
Why NHIs Are Security’s Most Dangerous Blind Spot
When we talk about identity in cybersecurity, most people think of usernames, passwords, and the occasional MFA prompt.…
April 25, 2025
Researchers Identify Rack::Static Vulnerability Enabling Data Breaches in Ruby Servers
Cybersecurity researchers have disclosed three security flaws in the Rack Ruby web server interface that, if successfully exploited,…
April 25, 2025
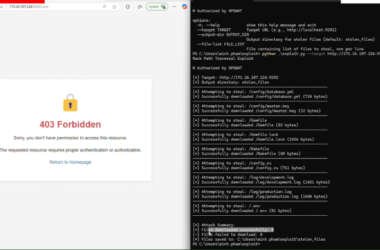
DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks
Cybersecurity researchers are warning about a new malware called DslogdRAT that’s installed following the exploitation of a now-patched…
April 25, 2025
Lazarus Hits 6 South Korean Firms via Cross EX, Innorix Flaws and ThreatNeedle Malware
At least six organizations in South Korea have been targeted by the prolific North Korea-linked Lazarus Group as…
April 24, 2025
Linux io_uring PoC Rootkit Bypasses System Call-Based Threat Detection Tools
Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a Linux asynchronous I/O mechanism called…
April 24, 2025
Automating Zero Trust in Healthcare: From Risk Scoring to Dynamic Policy Enforcement Without Network Redesign
The Evolving Healthcare Cybersecurity Landscape Healthcare organizations face unprecedented cybersecurity challenges in 2025. With operational technology (OT) environments…
April 24, 2025
159 CVEs Exploited in Q1 2025 — 28.3% Within 24 Hours of Disclosure
As many as 159 CVE identifiers have been flagged as exploited in the wild in the first quarter…
April 24, 2025
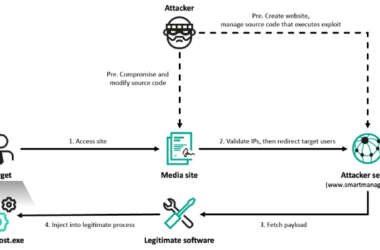
Darcula Adds GenAI to Phishing Toolkit, Lowering the Barrier for Cybercriminals
The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to their cybercrime suite with…
April 24, 2025