Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan
Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as…
April 21, 2025
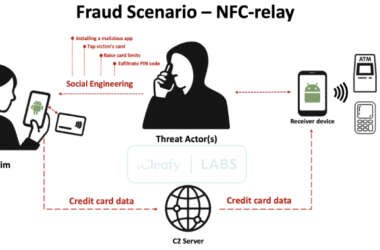
SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks
A new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication (NFC) relay attacks, enabling cybercriminals…
April 21, 2025
5 Reasons Device Management Isn’t Device Trust
The problem is simple: all breaches start with initial access, and initial access comes down to two primary…
April 21, 2025
⚡ THN Weekly Recap: iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More
Can a harmless click really lead to a full-blown cyberattack? Surprisingly, yes — and that’s exactly what we…
April 21, 2025
Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery
Cybersecurity researchers have disclosed a surge in “mass scanning, credential brute-forcing, and exploitation attempts” originating from IP addresses…
April 21, 2025
APT29 Deploys GRAPELOADER Malware Targeting European Diplomats Through Wine-Tasting Lures
The Russian state-sponsored threat actor known as APT29 has been linked to an advanced phishing campaign that’s targeting…
April 20, 2025
Rogue npm Packages Mimic Telegram Bot API to Plant SSH Backdoors on Linux Systems
Cybersecurity researchers have uncovered three malicious packages in the npm registry that masquerade as a popular Telegram bot…
April 19, 2025
ASUS Confirms Critical Flaw in AiCloud Routers; Users Urged to Update Firmware
ASUS has disclosed a critical security flaw impacting routers with AiCloud enabled that could permit remote attackers to…
April 19, 2025
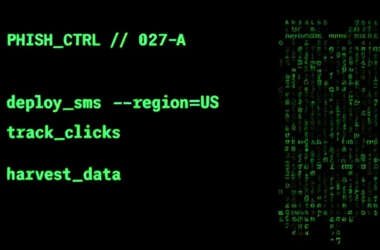
Chinese Smishing Kit Powers Widespread Toll Fraud Campaign Targeting U.S. Users in 8 States
Cybersecurity researchers are warning of a “widespread and ongoing” SMS phishing campaign that’s been targeting toll road users…
April 18, 2025
Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader.…
April 18, 2025