Gamma AI Platform Abused in Phishing Chain to Spoof Microsoft SharePoint Logins
Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct…
April 16, 2025
From Third-Party Vendors to U.S. Tariffs: The New Cyber Risks Facing Supply Chains
Introduction Cyber threats targeting supply chains have become a growing concern for businesses across industries. As companies continue…
April 16, 2025
New BPFDoor Controller Enables Stealthy Lateral Movement in Linux Server Attacks
Cybersecurity researchers have unearthed a new controller component associated with a known backdoor called BPFDoor as part of…
April 16, 2025
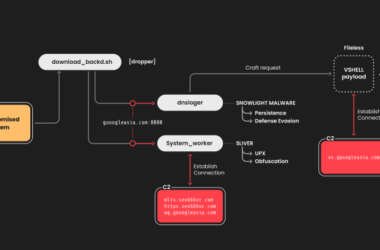
Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool
The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant…
April 15, 2025
Critical Apache Roller Vulnerability (CVSS 10.0) Enables Unauthorized Session Persistence
A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based blogging server software that could…
April 15, 2025
Majority of Browser Extensions Can Access Sensitive Enterprise Data, New Report Finds
Everybody knows browser extensions are embedded into nearly every user’s daily workflow, from spell checkers to GenAI tools.…
April 15, 2025
Malicious PyPI Package Targets MEXC Trading API to Steal Credentials and Redirect Orders
Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package Index (PyPI) repository that’s designed to…
April 15, 2025
Crypto Developers Targeted by Python Malware Disguised as Coding Challenges
The North Korea-linked threat actor assessed to be behind the massive Bybit hack in February 2025 has been…
April 15, 2025
ResolverRAT Campaign Targets Healthcare, Pharma via Phishing and DLL Side-Loading
Cybersecurity researchers have discovered a new, sophisticated remote access trojan called ResolverRAT that has been observed in attacks…
April 14, 2025
Phishing Campaigns Use Real-Time Checks to Validate Victim Emails Before Credential Theft
Cybersecurity researchers are calling attention to a new type of credential phishing scheme that ensures that the stolen…
April 14, 2025