New Chrome Zero-Day (CVE-2026-2441) Under Active Attack — Patch Released
Google on Friday released security updates for its Chrome browser to address a security flaw that it said…
February 16, 2026
Microsoft Discloses DNS-Based ClickFix Attack Using Nslookup for Malware Staging
Microsoft has disclosed details of a new version of the ClickFix social engineering tactic in which the attackers…
February 15, 2026
Google Ties Suspected Russian Actor to CANFAIL Malware Attacks on Ukrainian Orgs
A previously undocumented threat actor has been attributed to attacks targeting Ukrainian organizations with malware known as CANFAIL.…
February 13, 2026
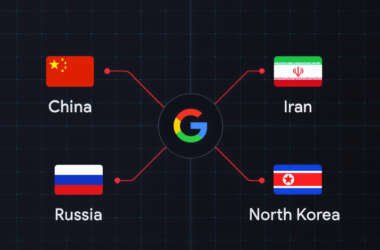
Google Links China, Iran, Russia, North Korea to Coordinated Defense Sector Cyber Operations
Several state-sponsored actors, hacktivist entities, and criminal groups from China, Iran, North Korea, and Russia have trained their…
February 13, 2026
UAT-9921 Deploys VoidLink Malware to Target Technology and Financial Sectors
A previously unknown threat actor tracked as UAT-9921 has been observed leveraging a new modular framework called VoidLink…
February 13, 2026
Malicious Chrome Extensions Caught Stealing Business Data, Emails, and Browsing History
Cybersecurity researchers have discovered a malicious Google Chrome extension that’s designed to steal data associated with Meta Business…
February 13, 2026
npm’s Update to Harden Their Supply Chain, and Points to Consider
In December 2025, in response to the Sha1-Hulud incident, npm completed a major authentication overhaul intended to reduce…
February 13, 2026
Google Reports State-Backed Hackers Using Gemini AI for Recon and Attack Support
Google on Thursday said it observed the North Korea-linked threat actor known as UNC2970 using its generative artificial…
February 12, 2026
Lazarus Campaign Plants Malicious Packages in npm and PyPI Ecosystems
Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI)…
February 12, 2026
ThreatsDay Bulletin: AI Prompt RCE, Claude 0-Click, RenEngine Loader, Auto 0-Days & 25+ Stories
Threat activity this week shows one consistent signal — attackers are leaning harder on what already works. Instead…
February 12, 2026