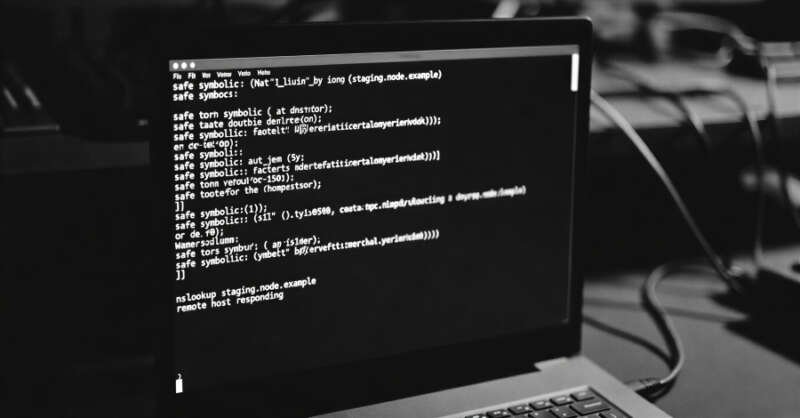
Microsoft has disclosed details of a new version of the ClickFix social engineering tactic in which the attackers trick unsuspecting users into running commands that carry out a Domain Name System (DNS) lookup to retrieve the next-stage payload.
Specifically, the attack relies on using the “nslookup” (short for nameserver lookup) command to execute a custom DNS lookup triggered via the Windows
Microsoft Discloses DNS-Based ClickFix Attack Using Nslookup for Malware Staging