Here’s the recreated walkthrough as Vansh Shrivastava:
TryHackMe Room: Chrome Challenge
Operating Systems: Windows, Kali
Difficulty: Hard
Category: Forensics
A password manager’s security is only as strong as the password protecting it. In this challenge, a malicious actor extracted something over the network, and our task is to figure out what it was. After downloading and extracting the provided chromefiles.zip, let’s dive in to answer the questions.

Questions to Answer:
- What is the first password we find?
- What is the URL in the first index (fully defanged)?
- What is the password in the first index?
- What is the URL in the second index (fully defanged)?
- What is the password in the second index?
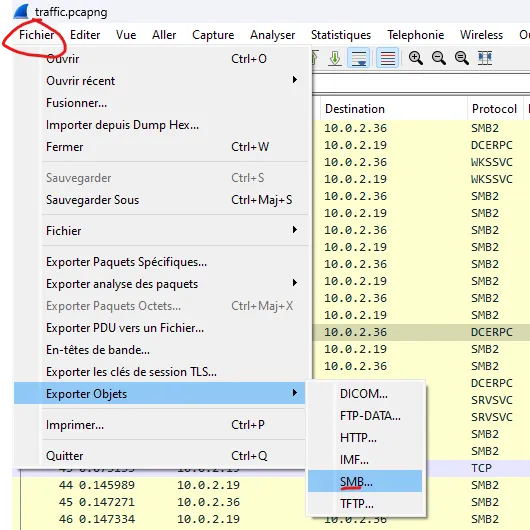
Step 1: Analyzing PcapNG with Wireshark
After extracting the zip file, I opened the pcapng file with Wireshark. The TCP handshake and several SMB2 packets were visible. Though SMB2 uses AES encryption, we can still see file requests in plain text. The goal here is to rebuild the files based on these requests.
Step 2: Reverse Engineering with dnSpy
Next, I used dnSpy to analyze the transfer.exe file. The key and IV vector needed for decryption were retrieved from the file, as shown in the screenshot provided. This is critical for decrypting the next step.

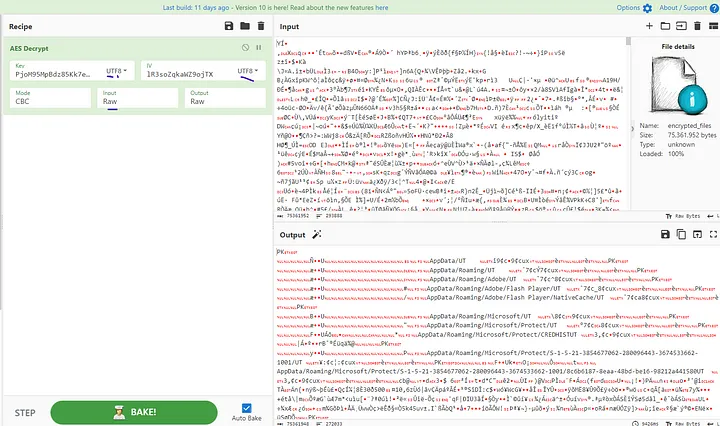
Step 3: Decrypting the File with CyberChef
With the key and IV vector, I turned to CyberChef to decrypt the file using AES. After adjusting the parameters, plain text data appeared. CyberChef identified the file as a zip, so I downloaded and extracted it to obtain the AppData file.

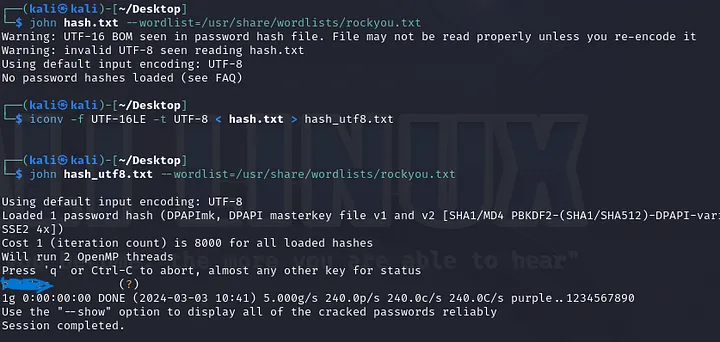
Step 4: Getting the Hash with DPAPImk2john
Using the DPAPImk2john script, I was able to extract the user’s hash from the AppData file.

Step 5: Cracking the Password with John the Ripper
Switching over to Kali, I cracked the hash using John the Ripper with the rockyou wordlist. The hash file needed to be recoded to UTF-8 first, but after running the cracker, the first password was found in seconds.
Step 6: Getting the AES Key with Mimikatz
To decrypt the master key, I employed Mimikatz, a well-known tool in both cybersecurity and hacking circles. After decoding the relevant file, I used the following Python script to decrypt the private AES key:
import json
import base64
fh = open('AppData/Local/Google/Chrome/User Data/Local State', 'rb')
encrypted_key = json.load(fh)
encrypted_key = encrypted_key['os_crypt']['encrypted_key']
decrypted_key = base64.b64decode(encrypted_key)
open("dec_data",'wb').write(decrypted_key[5:])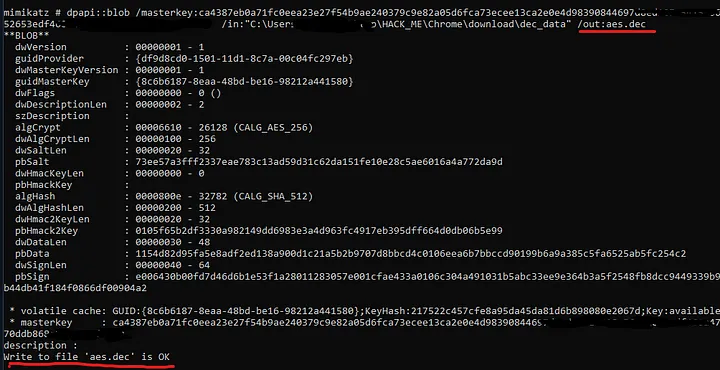
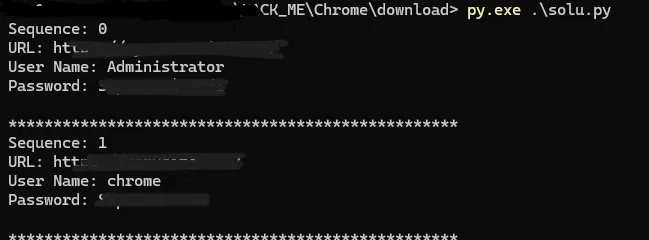
Step 7: Extracting Chrome Credentials
With the decrypted AES key in hand, I modified a script to extract the passwords stored in Chrome. After running it, the passwords and associated URLs were displayed in the console.
Reflections:
This room was a blend of medium and hard difficulty. What made this challenge especially engaging was how it intersected with my current exploration of Google Chrome’s password manager through a BadUSB payload. It required a solid understanding of reverse engineering and cryptography, which made the room both educational and enjoyable.
That’s my walkthrough of the TryHackMe Chrome Challenge, and it provided an excellent opportunity to sharpen key skills while solving a realistic forensic challenge.








