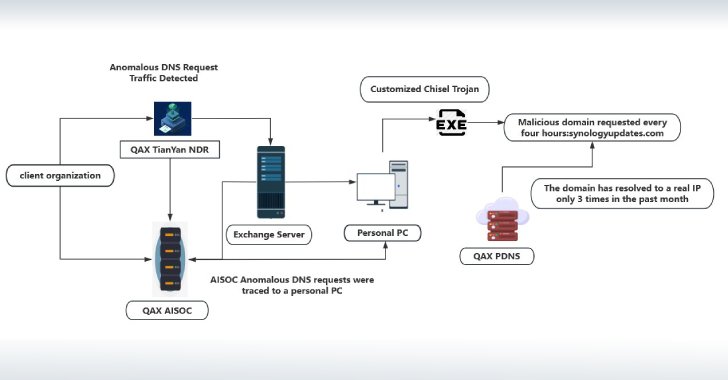
Cybersecurity researchers have shed light on a previously undocumented threat actor called NightEagle (aka APT-Q-95) that has been observed targeting Microsoft Exchange servers as a part of a zero-day exploit chain designed to target government, defense, and technology sectors in China.
According to QiAnXin’s RedDrip Team, the threat actor has been active since 2023 and has switched network
NightEagle APT Exploits Microsoft Exchange Flaw to Target China’s Military and Tech Sectors