Gainsight Expands Impacted Customer List Following Salesforce Security Alert
Gainsight has disclosed that the recent suspicious activity targeting its applications has affected more customers than previously thought.…
November 27, 2025
Shai-Hulud v2 Spreads From npm to Maven, as Campaign Exposes Thousands of Secrets
The second wave of the Shai-Hulud supply chain attack has spilled over to the Maven ecosystem after compromising…
November 26, 2025
Qilin Ransomware Turns South Korean MSP Breach Into 28-Victim ‘Korean Leaks’ Data Heist
South Korea’s financial sector has been targeted by what has been described as a sophisticated supply chain attack…
November 26, 2025
When Your $2M Security Detection Fails: Can your SOC Save You?
Enterprises today are expected to have at least 6-8 detection tools, as detection is considered a standard investment…
November 26, 2025
Chrome Extension Caught Injecting Hidden Solana Transfer Fees Into Raydium Swaps
Cybersecurity researchers have discovered a new malicious extension on the Chrome Web Store that’s capable of injecting a…
November 26, 2025
Webinar: Learn to Spot Risks and Patch Safely with Community-Maintained Tools
If you’re using community tools like Chocolatey or Winget to keep systems updated, you’re not alone. These platforms…
November 26, 2025
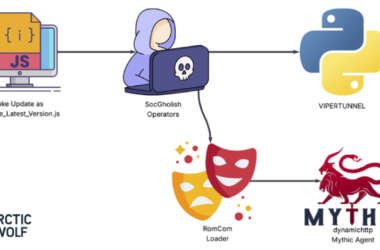
RomCom Uses SocGholish Fake Update Attacks to Deliver Mythic Agent Malware
The threat actors behind a malware family known as RomCom targeted a U.S.-based civil engineering company via a…
November 26, 2025
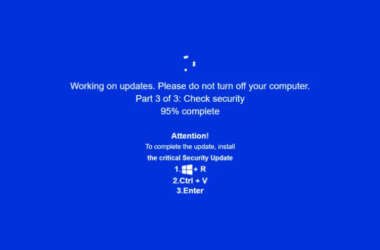
JackFix Uses Fake Windows Update Pop-Ups on Adult Sites to Deliver Multiple Stealers
Cybersecurity researchers are calling attention to a new campaign that’s leveraging a combination of ClickFix lures and fake…
November 25, 2025
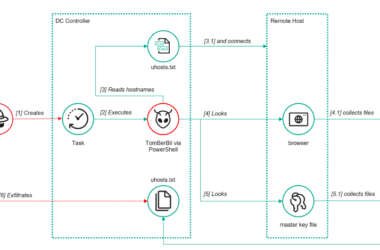
ToddyCat’s New Hacking Tools Steal Outlook Emails and Microsoft 365 Access Tokens
The threat actor known as ToddyCat has been observed adopting new methods to obtain access to corporate email…
November 25, 2025
3 SOC Challenges You Need to Solve Before 2026
2026 will mark a pivotal shift in cybersecurity. Threat actors are moving from experimenting with AI to making…
November 25, 2025