⚡ Weekly Recap: Lazarus Hits Web3, Intel/AMD TEEs Cracked, Dark Web Leak Tool & More
Cyberattacks are getting smarter and harder to stop. This week, hackers used sneaky tools, tricked trusted systems, and…
November 3, 2025
The Evolution of SOC Operations: How Continuous Exposure Management Transforms Security Operations
Security Operations Centers (SOC) today are overwhelmed. Analysts handle thousands of alerts every day, spending much time chasing…
November 3, 2025
Researchers Uncover BankBot-YNRK and DeliveryRAT Android Trojans Stealing Financial Data
Cybersecurity researchers have shed light on two different Android trojans called BankBot-YNRK and DeliveryRAT that are capable of…
November 3, 2025
New HttpTroy Backdoor Poses as VPN Invoice in Targeted Cyberattack on South Korea
The North Korea-linked threat actor known as Kimsuky has distributed a previously undocumented backdoor codenamed HttpTroy as part…
November 3, 2025
ASD Warns of Ongoing BADCANDY Attacks Exploiting Cisco IOS XE Vulnerability
The Australian Signals Directorate (ASD) has issued a bulletin about ongoing cyber attacks targeting unpatched Cisco IOS XE…
November 1, 2025
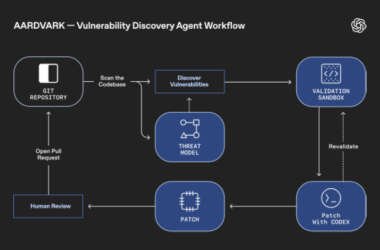
OpenAI Unveils Aardvark: GPT-5 Agent That Finds and Fixes Code Flaws Automatically
OpenAI has announced the launch of an “agentic security researcher” that’s powered by its GPT-5 large language model…
October 31, 2025
Nation-State Hackers Deploy New Airstalk Malware in Suspected Supply Chain Attack
A suspected nation-state threat actor has been linked to the distribution of a new malware called Airstalk as…
October 31, 2025
China-Linked Hackers Exploit Windows Shortcut Flaw to Target European Diplomats
A China-affiliated threat actor known as UNC6384 has been linked to a fresh set of attacks exploiting an…
October 31, 2025
China-Linked Tick Group Exploits Lanscope Zero-Day to Hijack Corporate Systems
The exploitation of a recently disclosed critical security flaw in Motex Lanscope Endpoint Manager has been attributed to…
October 31, 2025
The MSP Cybersecurity Readiness Guide: Turning Security into Growth
MSPs are facing rising client expectations for strong cybersecurity and compliance outcomes, while threats grow more complex and…
October 31, 2025