⚡ Weekly Recap: Bootkit Malware, AI-Powered Attacks, Supply Chain Breaches, Zero-Days & More
In a world where threats are persistent, the modern CISO’s real job isn’t just to secure technology—it’s to…
September 15, 2025
AI-Powered Villager Pen Testing Tool Hits 11,000 PyPI Downloads Amid Abuse Concerns
A new artificial intelligence (AI)-powered penetration testing tool linked to a China-based company has attracted nearly 11,000 downloads…
September 15, 2025
HiddenGh0st, Winos and kkRAT Exploit SEO, GitHub Pages in Chinese Malware Attacks
Chinese-speaking users are the target of a search engine optimization (SEO) poisoning campaign that uses fake software sites…
September 15, 2025
FBI Warns of UNC6040 and UNC6395 Targeting Salesforce Platforms in Data Theft Attacks
The U.S. Federal Bureau of Investigation (FBI) has issued a flash alert to release indicators of compromise (IoCs)…
September 13, 2025
Samsung Fixes Critical Zero-Day CVE-2025-21043 Exploited in Android Attacks
Samsung has released its monthly security updates for Android, including a fix for a security vulnerability that it…
September 12, 2025
Apple Warns French Users of Fourth Spyware Campaign in 2025, CERT-FR Confirms
Apple has notified users in France of a spyware campaign targeting their devices, according to the Computer Emergency…
September 12, 2025
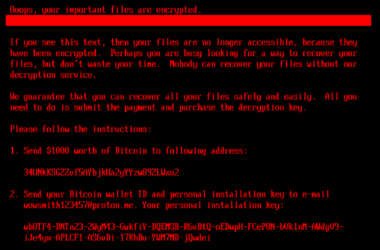
New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344 Exploit
Cybersecurity researchers have discovered a new ransomware strain dubbed HybridPetya that resembles the notorious Petya/NotPetya malware, while also…
September 12, 2025
Critical CVE-2025-5086 in DELMIA Apriso Actively Exploited, CISA Issues Warning
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Dassault Systèmes…
September 12, 2025
Cloud-Native Security in 2025: Why Runtime Visibility Must Take Center Stage
The security landscape for cloud-native applications is undergoing a profound transformation. Containers, Kubernetes, and serverless technologies are now…
September 12, 2025
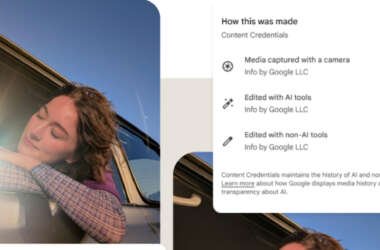
Google Pixel 10 Adds C2PA Support to Verify AI-Generated Media Authenticity
Google on Tuesday announced that its new Google Pixel 10 phones support the Coalition for Content Provenance and…
September 11, 2025