Detecting Data Leaks Before Disaster
In January 2025, cybersecurity experts at Wiz Research found that Chinese AI specialist DeepSeek had suffered a data…
September 3, 2025
Android Security Alert: Google Patches 120 Flaws, Including Two Zero-Days Under Attack
Google has shipped security updates to address 120 security flaws in its Android operating system as part of…
September 3, 2025
Iranian Hackers Exploit 100+ Embassy Email Accounts in Global Phishing Targeting Diplomats
An Iran-nexus group has been linked to a “coordinated” and “multi-wave” spear-phishing campaign targeting the embassies and consulates…
September 3, 2025
Researchers Warn of MystRodX Backdoor Using DNS and ICMP Triggers for Stealthy Control
Cybersecurity researchers have disclosed a stealthy new backdoor called MystRodX that comes with a variety of features to…
September 2, 2025
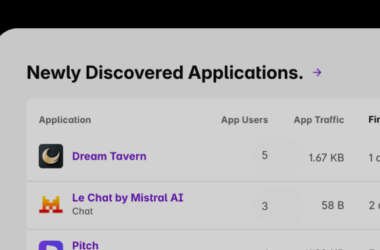
Shadow AI Discovery: A Critical Part of Enterprise AI Governance
The Harsh Truths of AI Adoption MITs State of AI in Business report revealed that while 40% of…
September 2, 2025
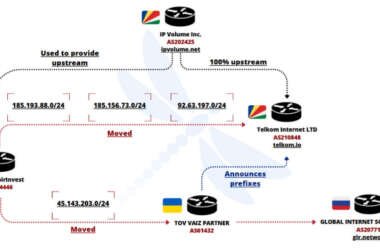
Ukrainian Network FDN3 Launches Massive Brute-Force Attacks on SSL VPN and RDP Devices
Cybersecurity researchers have flagged a Ukrainian IP network for engaging in massive brute-force and password spraying campaigns targeting…
September 2, 2025
Silver Fox Exploits Microsoft-Signed WatchDog Driver to Deploy ValleyRAT Malware
The threat actor known as Silver Fox has been attributed to abuse of a previously unknown vulnerable driver…
September 2, 2025
Malicious npm Package nodejs-smtp Mimics Nodemailer, Targets Atomic and Exodus Wallets
Cybersecurity researchers have discovered a malicious npm package that comes with stealthy features to inject malicious code into…
September 2, 2025
⚡ Weekly Recap: WhatsApp 0-Day, Docker Bug, Salesforce Breach, Fake CAPTCHAs, Spyware App & More
Cybersecurity today is less about single attacks and more about chains of small weaknesses that connect into big…
September 1, 2025
When Browsers Become the Attack Surface: Rethinking Security for Scattered Spider
As enterprises continue to shift their operations to the browser, security teams face a growing set of cyber…
September 1, 2025