RoguePilot Flaw in GitHub Codespaces Enabled Copilot to Leak GITHUB_TOKEN
A vulnerability in GitHub Codespaces could have been exploited by bad actors to seize control of repositories by…
February 24, 2026
UAC-0050 Targets European Financial Institution With Spoofed Domain and RMS Malware
A Russia-aligned threat actor has been observed targeting a European financial institution as part of a social engineering…
February 24, 2026
Anthropic Says Chinese AI Firms Used 16 Million Claude Queries to Copy Model
Anthropic on Monday said it identified “industrial-scale campaigns” mounted by three artificial intelligence (AI) companies, DeepSeek, Moonshot AI,…
February 24, 2026
APT28 Targeted European Entities Using Webhook-Based Macro Malware
The Russia-linked state-sponsored threat actor tracked as APT28 has been attributed to a new campaign targeting specific entities…
February 23, 2026
Wormable XMRig Campaign Uses BYOVD Exploit and Time-Based Logic Bomb
Cybersecurity researchers have disclosed details of a new cryptojacking campaign that uses pirated software bundles as lures to…
February 23, 2026
⚡ Weekly Recap: Double-Tap Skimmers, PromptSpy AI, 30Tbps DDoS, Docker Malware & More
Security news rarely moves in a straight line. This week, it feels more like a series of sharp…
February 23, 2026
How Exposed Endpoints Increase Risk Across LLM Infrastructure
As more organizations run their own Large Language Models (LLMs), they are also deploying more internal services and…
February 23, 2026
MuddyWater Targets MENA Organizations with GhostFetch, CHAR, and HTTP_VIP
The Iranian hacking group known as MuddyWater (aka Earth Vetala, Mango Sandstorm, and MUDDYCOAST) has targeted several organizations…
February 23, 2026
AI-Assisted Threat Actor Compromises 600+ FortiGate Devices in 55 Countries
A Russian-speaking, financially motivated threat actor has been observed taking advantage of commercial generative artificial intelligence (AI) services…
February 21, 2026
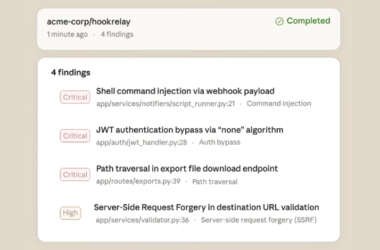
Anthropic Launches Claude Code Security for AI-Powered Vulnerability Scanning
Artificial intelligence (AI) company Anthropic has begun to roll out a new security feature for Claude Code that…
February 21, 2026