Google Launches DBSC Open Beta in Chrome and Enhances Patch Transparency via Project Zero
Google has announced that it’s making a security feature called Device Bound Session Credentials (DBSC) in open beta…
July 30, 2025
Chaos RaaS Emerges After BlackSuit Takedown, Demanding $300K from U.S. Victims
A newly emerged ransomware-as-a-service (RaaS) gang called Chaos is likely made up of former members of the BlackSuit…
July 29, 2025
How the Browser Became the Main Cyber Battleground
Until recently, the cyber attacker methodology behind the biggest breaches of the last decade or so has been…
July 29, 2025
Cybercriminals Use Fake Apps to Steal Data and Blackmail Users Across Asia’s Mobile Networks
Cybersecurity researchers have discovered a new, large-scale mobile malware campaign that’s targeting Android and iOS platforms with fake…
July 29, 2025
Why React Didn’t Kill XSS: The New JavaScript Injection Playbook
React conquered XSS? Think again. That’s the reality facing JavaScript developers in 2025, where attackers have quietly evolved…
July 29, 2025
CISA Adds PaperCut NG/MF CSRF Vulnerability to KEV Catalog Amid Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a high-severity security vulnerability impacting PaperCutNG/MF print…
July 29, 2025
⚡ Weekly Recap — SharePoint Breach, Spyware, IoT Hijacks, DPRK Fraud, Crypto Drains and More
Some risks don’t breach the perimeter—they arrive through signed software, clean resumes, or sanctioned vendors still hiding in…
July 28, 2025
Email Security Is Stuck in the Antivirus Era: Why It Needs a Modern Approach
Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But…
July 28, 2025
Scattered Spider Hijacks VMware ESXi to Deploy Ransomware on Critical U.S. Infrastructure
The notorious cybercrime group known as Scattered Spider is targeting VMware ESXi hypervisors in attacks targeting retail, airline,…
July 28, 2025
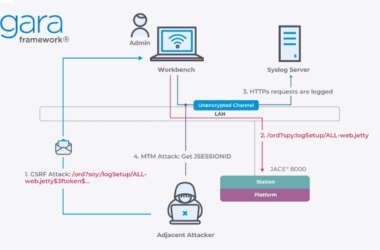
Critical Flaws in Niagara Framework Threaten Smart Buildings and Industrial Systems Worldwide
Cybersecurity researchers have discovered over a dozen security vulnerabilities impacting Tridium’s Niagara Framework that could allow an attacker…
July 28, 2025