The Unusual Suspect: Git Repos
While phishing and ransomware dominate headlines, another critical risk quietly persists across most enterprises: exposed Git repositories leaking…
July 14, 2025
⚡ Weekly Recap: Scattered Spider Arrests, Car Exploits, macOS Malware, Fortinet RCE and More
In cybersecurity, precision matters—and there’s little room for error. A small mistake, missed setting, or quiet misconfiguration can…
July 14, 2025
CBI Shuts Down £390K U.K. Tech Support Scam, Arrests Key Operatives in Noida Call Center
India’s Central Bureau of Investigation (CBI) has announced that it has taken steps to dismantle what it said…
July 14, 2025
eSIM Vulnerability in Kigen’s eUICC Cards Exposes Billions of IoT Devices to Malicious Attacks
Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the eSIM technology used in modern…
July 14, 2025
GPUHammer: New RowHammer Attack Variant Degrades AI Models on NVIDIA GPUs
NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of…
July 12, 2025
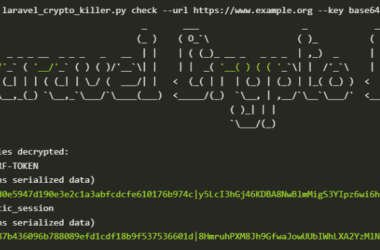
Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub
Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain…
July 12, 2025
Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257)
Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to…
July 11, 2025
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution
Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully…
July 11, 2025
Securing Data in the AI Era
The 2025 Data Risk Report: Enterprises face potentially serious data loss risks from AI-fueled tools. Adopting a unified,…
July 11, 2025
Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild
A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come under active exploitation in the…
July 11, 2025