Citizen Lab Finds Cellebrite Tool Used on Kenyan Activist’s Phone in Police Custody
New research from the Citizen Lab has found signs that Kenyan authorities used a commercial forensic extraction tool…
February 18, 2026
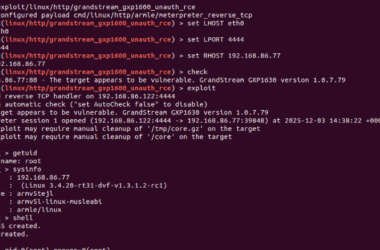
Grandstream GXP1600 VoIP Phones Exposed to Unauthenticated Remote Code Execution
Cybersecurity researchers have disclosed a critical security flaw in the Grandstream GXP1600 series of VoIP phones that could…
February 18, 2026
Critical Flaws Found in Four VS Code Extensions with Over 125 Million Installs
Cybersecurity researchers have disclosed multiple security vulnerabilities in four popular Microsoft Visual Studio Code (VS Code) extensions that,…
February 18, 2026
Cybersecurity Tech Predictions for 2026: Operating in a World of Permanent Instability
In 2025, navigating the digital seas still felt like a matter of direction. Organizations charted routes, watched the…
February 18, 2026
Notepad++ Fixes Hijacked Update Mechanism Used to Deliver Targeted Malware
Notepad++ has released a security fix to plug gaps that were exploited by an advanced threat actor from…
February 18, 2026
CISA Flags Four Security Flaws Under Active Exploitation in Latest KEV Update
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added four security flaws to its Known Exploited…
February 18, 2026
Webinar: How Modern SOC Teams Use AI and Context to Investigate Cloud Breaches Faster
Cloud attacks move fast — faster than most incident response teams. In data centers, investigations had time. Teams…
February 17, 2026
Researchers Show Copilot and Grok Can Be Abused as Malware C2 Proxies
Cybersecurity researchers have disclosed that artificial intelligence (AI) assistants that support web browsing or URL fetching capabilities can…
February 17, 2026
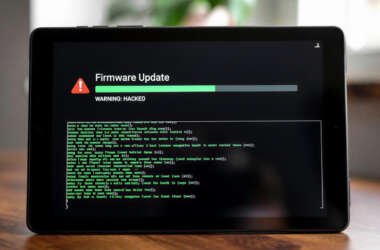
Keenadu Firmware Backdoor Infects Android Tablets via Signed OTA Updates
A new Android backdoor that’s embedded deep into the device firmware can silently harvest data and remotely control…
February 17, 2026
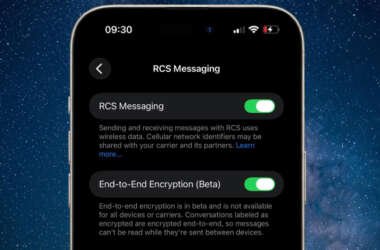
Apple Tests End-to-End Encrypted RCS Messaging in iOS 26.4 Developer Beta
Apple on Monday released a new developer beta of iOS and iPadOS with support for end-to-end encryption (E2EE)…
February 17, 2026