SentinelOne Uncovers Chinese Espionage Campaign Targeting Its Infrastructure and Clients
Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure…
April 29, 2025
Product Walkthrough: Securing Microsoft Copilot with Reco
Find out how Reco keeps Microsoft 365 Copilot safe by spotting risky prompts, protecting data, managing user access,…
April 29, 2025
Google Reports 75 Zero-Days Exploited in 2024 — 44% Targeted Enterprise Security Products
Google has revealed that it observed 75 zero-day vulnerabilities exploited in the wild in 2024, down from 98…
April 29, 2025
⚡ Weekly Recap: Critical SAP Exploit, AI-Powered Phishing, Major Breaches, New CVEs & More
What happens when cybercriminals no longer need deep skills to breach your defenses? Today’s attackers are armed with…
April 28, 2025
How Breaches Start: Breaking Down 5 Real Vulns
Not every security vulnerability is high risk on its own – but in the hands of an advanced…
April 28, 2025
Earth Kurma Targets Southeast Asia With Rootkits and Cloud-Based Data Theft Tools
Government and telecommunications sectors in Southeast Asia have become the target of a “sophisticated” campaign undertaken by a…
April 28, 2025
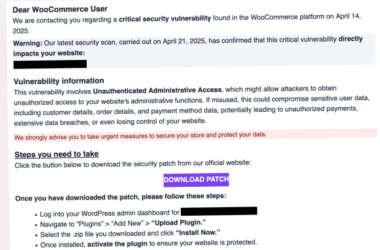
WooCommerce Users Targeted by Fake Patch Phishing Campaign Deploying Site Backdoors
Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with a fake security alert urging…
April 28, 2025
Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised
Threat actors have been observed exploiting two newly disclosed critical security flaws in Craft CMS in zero-day attacks…
April 28, 2025
Storm-1977 Hits Education Clouds with AzureChecker, Deploys 200+ Crypto Mining Containers
Microsoft has revealed that a threat actor it tracks as Storm-1977 has conducted password spraying attacks against cloud…
April 27, 2025
ToyMaker Uses LAGTOY to Sell Access to CACTUS Ransomware Gangs for Double Extortion
Cybersecurity researchers have detailed the activities of an initial access broker (IAB) dubbed ToyMaker that has been observed…
April 26, 2025