DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack
Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of Korea or DPRK) have…
April 23, 2025
Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign
The Iran-nexus threat actor known as UNC2428 has been observed delivering a backdoor known as MURKYTOUR as part…
April 23, 2025
Android Spyware Disguised as Alpine Quest App Targets Russian Military Devices
Cybersecurity researchers have revealed that Russian military personnel are the target of a new malicious campaign that distributes…
April 23, 2025
Three Reasons Why the Browser is Best for Stopping Phishing Attacks
Phishing attacks remain a huge challenge for organizations in 2025. In fact, with attackers increasingly leveraging identity-based techniques…
April 23, 2025
Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp
Multiple suspected Russia-linked threat actors are “aggressively” targeting individuals and organizations with ties to Ukraine and human rights…
April 23, 2025
Docker Malware Exploits Teneo Web3 Node to Earn Crypto via Fake Heartbeat Signals
Cybersecurity researchers have detailed a malware campaign that’s targeting Docker environments with a previously undocumented technique to mine…
April 22, 2025
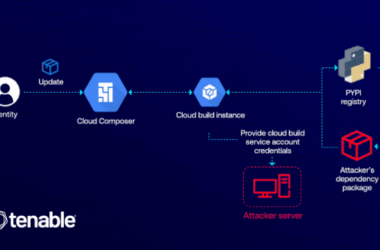
GCP Cloud Composer Bug Let Attackers Elevate Access via Malicious PyPI Packages
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker…
April 22, 2025
5 Major Concerns With Employees Using The Browser
As SaaS and cloud-native work reshape the enterprise, the web browser has emerged as the new endpoint. However,…
April 22, 2025
Phishers Exploit Google Sites and DKIM Replay to Send Signed Emails, Steal Credentials
In what has been described as an “extremely sophisticated phishing attack,” threat actors have leveraged an uncommon approach…
April 22, 2025
Microsoft Secures MSA Signing with Azure Confidential VMs Following Storm-0558 Breach
Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual…
April 22, 2025