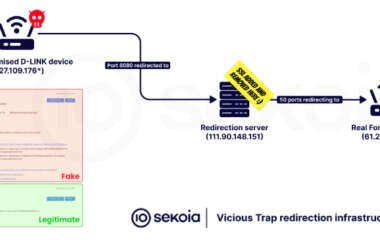
Some of the most devastating cyberattacks don’t rely on brute force, but instead succeed through stealth. These quiet intrusions often go unnoticed until long after the attacker has disappeared. Among the most insidious are man-in-the-middle (MITM) attacks, where criminals exploit weaknesses in communication protocols to silently position themselves between two unsuspecting parties
Man-in-the-Middle Attack Prevention Guide