North Korean Hackers Publish 26 npm Packages Hiding Pastebin C2 for Cross-Platform RAT
Cybersecurity researchers have disclosed a new iteration of the ongoing Contagious Interview campaign, where the North Korean threat…
March 2, 2026
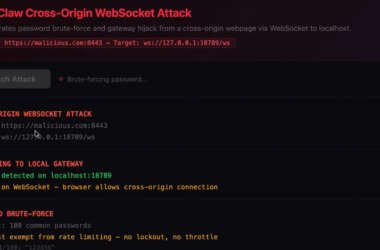
ClawJacked Flaw Lets Malicious Sites Hijack Local OpenClaw AI Agents via WebSocket
OpenClaw has fixed a high-severity security issue that, if successfully exploited, could have allowed a malicious website to…
February 28, 2026
Thousands of Public Google Cloud API Keys Exposed with Gemini Access After API Enablement
New research has found that Google Cloud API keys, typically designated as project identifiers for billing purposes, could…
February 28, 2026
Pentagon Designates Anthropic Supply Chain Risk Over AI Military Dispute
Anthropic on Friday hit back after U.S. Secretary of Defense Pete Hegseth directed the Pentagon to designate the…
February 28, 2026
DoJ Seizes $61 Million in Tether Linked to Pig Butchering Crypto Scams
The U.S. Department of Justice (DoJ) this week announced the seizure of $61 million worth of Tether that…
February 27, 2026
900+ Sangoma FreePBX Instances Compromised in Ongoing Web Shell Attacks
The Shadowserver Foundation has revealed that over 900 Sangoma FreePBX instances still remain infected with web shells as…
February 27, 2026
Malicious Go Crypto Module Steals Passwords, Deploys Rekoobe Backdoor
Cybersecurity researchers have disclosed details of a malicious Go module that’s designed to harvest passwords, create persistent access…
February 27, 2026
Meta Files Lawsuits Against Brazil, China, Vietnam Advertisers Over Celeb-Bait Scams
Meta on Thursday said it’s taking legal action to tackle scams on its platforms by filing lawsuits against…
February 27, 2026
Aeternum C2 Botnet Stores Encrypted Commands on Polygon Blockchain to Evade Takedown
Cybersecurity researchers have disclosed details of a new botnet loader called Aeternum C2 that uses a blockchain-based command-and-control…
February 26, 2026
UAT-10027 Targets U.S. Education and Healthcare with Dohdoor Backdoor
A previously undocumented threat activity cluster has been attributed to an ongoing malicious campaign targeting education and healthcare…
February 26, 2026