Cisco Warns of Critical ISE Flaw Allowing Unauthenticated Attackers to Execute Root Code
Cisco has disclosed a new maximum-severity security vulnerability impacting Identity Services Engine (ISE) and Cisco ISE Passive Identity…
July 17, 2025
UNC6148 Backdoors Fully-Patched SonicWall SMA 100 Series Devices with OVERSTEP Rootkit
A threat activity cluster has been observed targeting fully-patched end-of-life SonicWall Secure Mobile Access (SMA) 100 series appliances…
July 16, 2025
Critical Golden dMSA Attack in Windows Server 2025 Enables Cross-Domain Attacks and Persistent Access
Cybersecurity researchers have disclosed what they say is a “critical design flaw” in delegated Managed Service Accounts (dMSAs)…
July 16, 2025
AI Agents Act Like Employees With Root Access—Here’s How to Regain Control
The AI gold rush is on. But without identity-first security, every deployment becomes an open door. Most organizations…
July 16, 2025
Deepfakes. Fake Recruiters. Cloned CFOs — Learn How to Stop AI-Driven Attacks in Real Time
Social engineering attacks have entered a new era—and they’re coming fast, smart, and deeply personalized. It’s no longer…
July 16, 2025
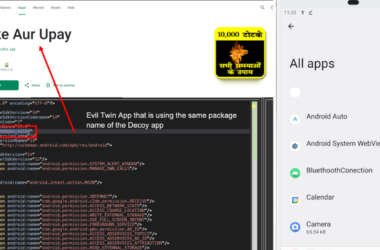
New Konfety Malware Variant Evades Detection by Manipulating APKs and Dynamic Code
Cybersecurity researchers have discovered a new, sophisticated variant of a known Android malware referred to as Konfety that…
July 16, 2025
State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments
Governmental organizations in Southeast Asia are the target of a new campaign that aims to collect sensitive information…
July 15, 2025
Securing Agentic AI: How to Protect the Invisible Identity Access
AI agents promise to automate everything from financial reconciliations to incident response. Yet every time an AI agent…
July 15, 2025
AsyncRAT’s Open-Source Code Sparks Surge in Dangerous Malware Variants Across the Globe
Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first…
July 15, 2025
North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign
The North Korean threat actors linked to the Contagious Interview campaign have been observed publishing another set of…
July 15, 2025